Blog
Security That Ships
Security, strategy, and developer-first thinking for teams pushing open-source forward.
This is some text inside of a div block.

Hopper Just Made Exploitability Verification Instant
Introducing Hopper Exploitability Verification. AI-driven analysis that confirms what is exploitable across your entire software ecosystem. Noise removed. Real impact verified.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

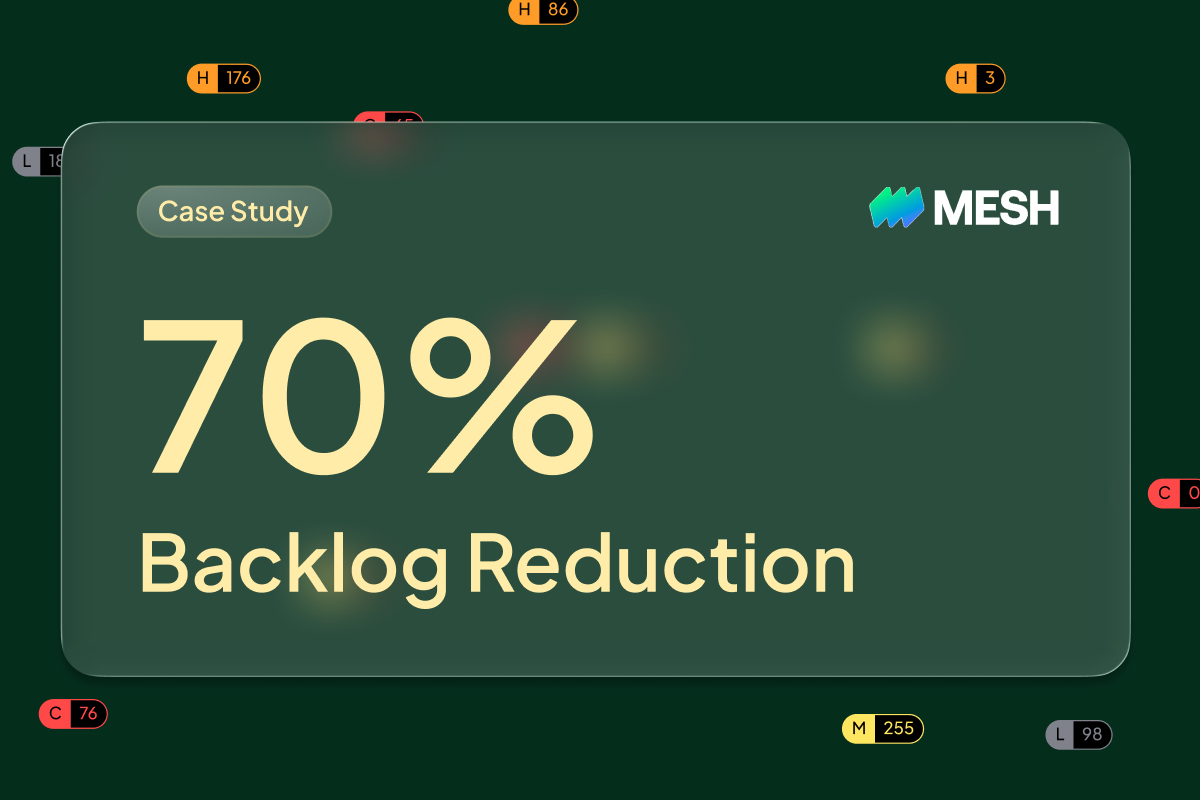
Mesh Escaped Dependency Hell and Achieved 70% Backlog Reduction with Hopper
Mesh Escaped Dependency Hell and Achieved 70% Backlog Reduction with Hopper
Mesh Payments eliminated 83% of security alert noise and reduced backlog by 70% using Hopper. They now remediate vulnerabilities 3x faster with early alerts and third-party dependency visibility.
Customer Stories


HPE Cuts Through Noise and Saves $1.4M with Hopper
HPE Cuts Through Noise and Saves $1.4M with Hopper
HPE replaced their legacy SCA tool with Hopper, reducing alert noise by 92% and accelerating incident response by 10x. The switch led to $1.4M in operational savings and significantly improved developer and security collaboration.
Customer Stories


The First Accurate Vulnerability Analysis for Django Applications
Hopper now provides the first accurate vulnerability analysis for Django applications by understanding dynamic behaviors like routing, decorators, and runtime context that traditional tools miss. With function-level reachability across transitive dependencies, Hopper identifies only the risks that are truly exploitable in production.
Product
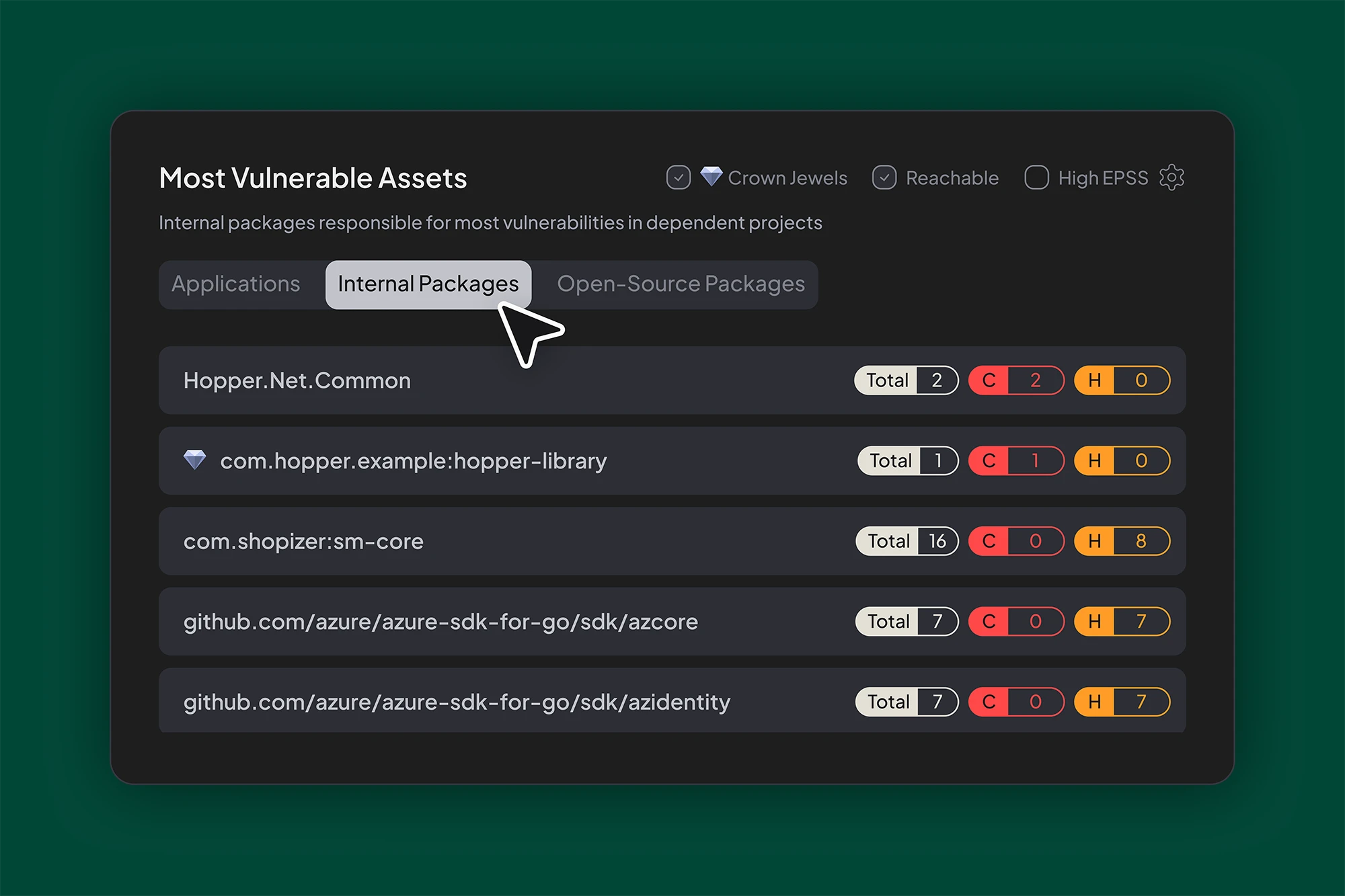

Internal Libraries: The Most Overlooked Attack Surface
Patching internal libraries isn’t enough if outdated versions are still pulled into production. Hopper exposes these hidden paths by tracing usage across services, identifying vulnerable versions, and prioritizing them using reachability and real-world exploitability.
Insights
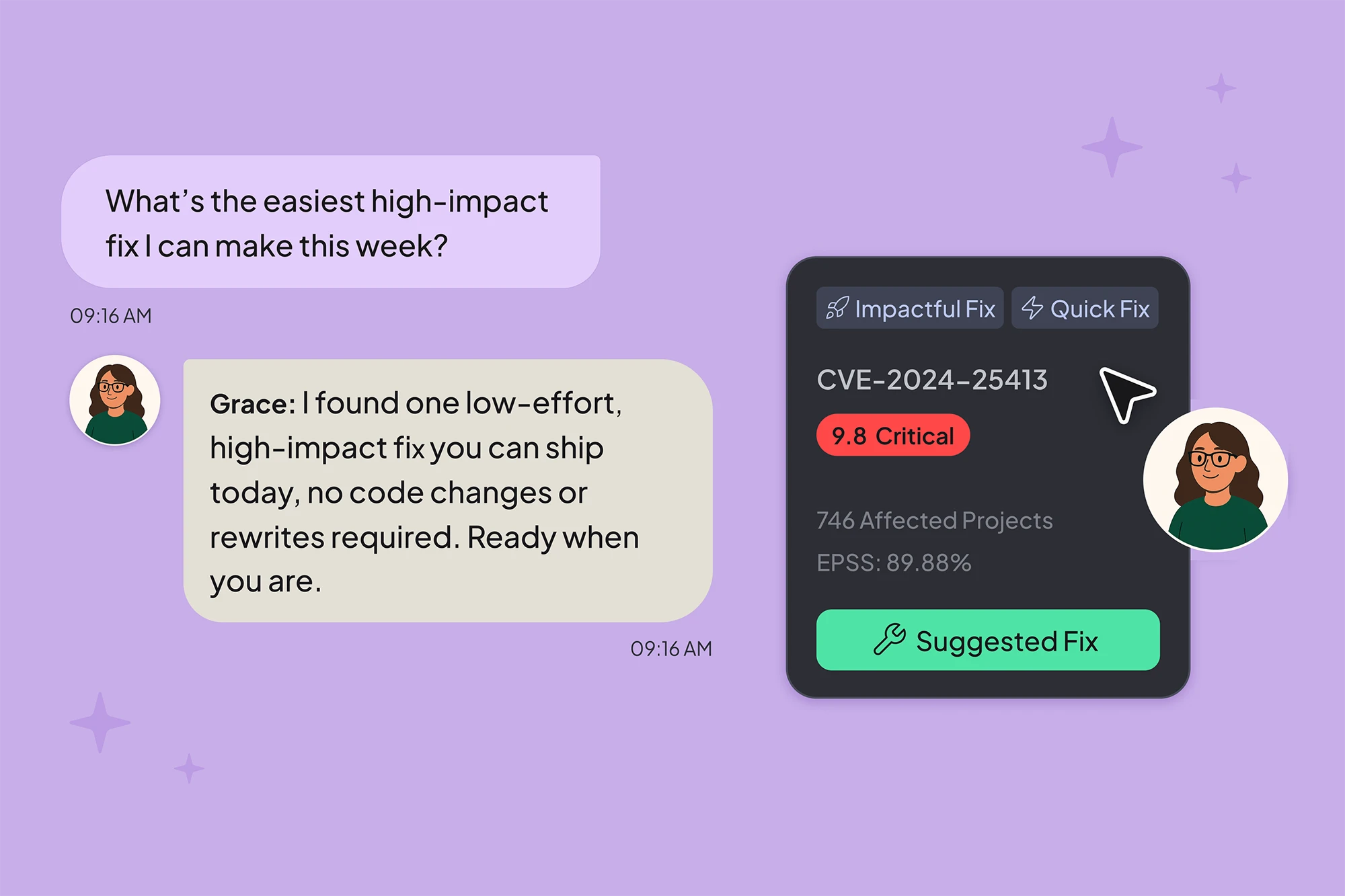

Meet Grace: Hopper’s AI-Powered MCP Server for Open-Source Security
Grace connects Hopper’s real-time data to AI agents through the Model Context Protocol (MCP), automating triage and remediation in minutes.
Product


How Hopper Builds Fix Plans Developers Actually Use
Hopper turns noisy vulnerability alerts into developer-ready fix plans using function-level reachability, call graph evidence, and effort-aware remediation. Learn how.
Insights

Hopper Launches Four AI-Powered AppSec Products for the Age of Modern Software
Traditional AppSec tools weren’t built for AI-powered development. Hopper’s new suite delivers visibility and control across open-source, embedded models, and AI-generated code.
Announcements


Hopper Maintains SOC 2 Type II and ISO 27001 Certifications
Hopper is SOC 2 Type II and ISO/IEC 27001 certified, demonstrating our commitment to enterprise-grade security and protecting customer data.
Announcements
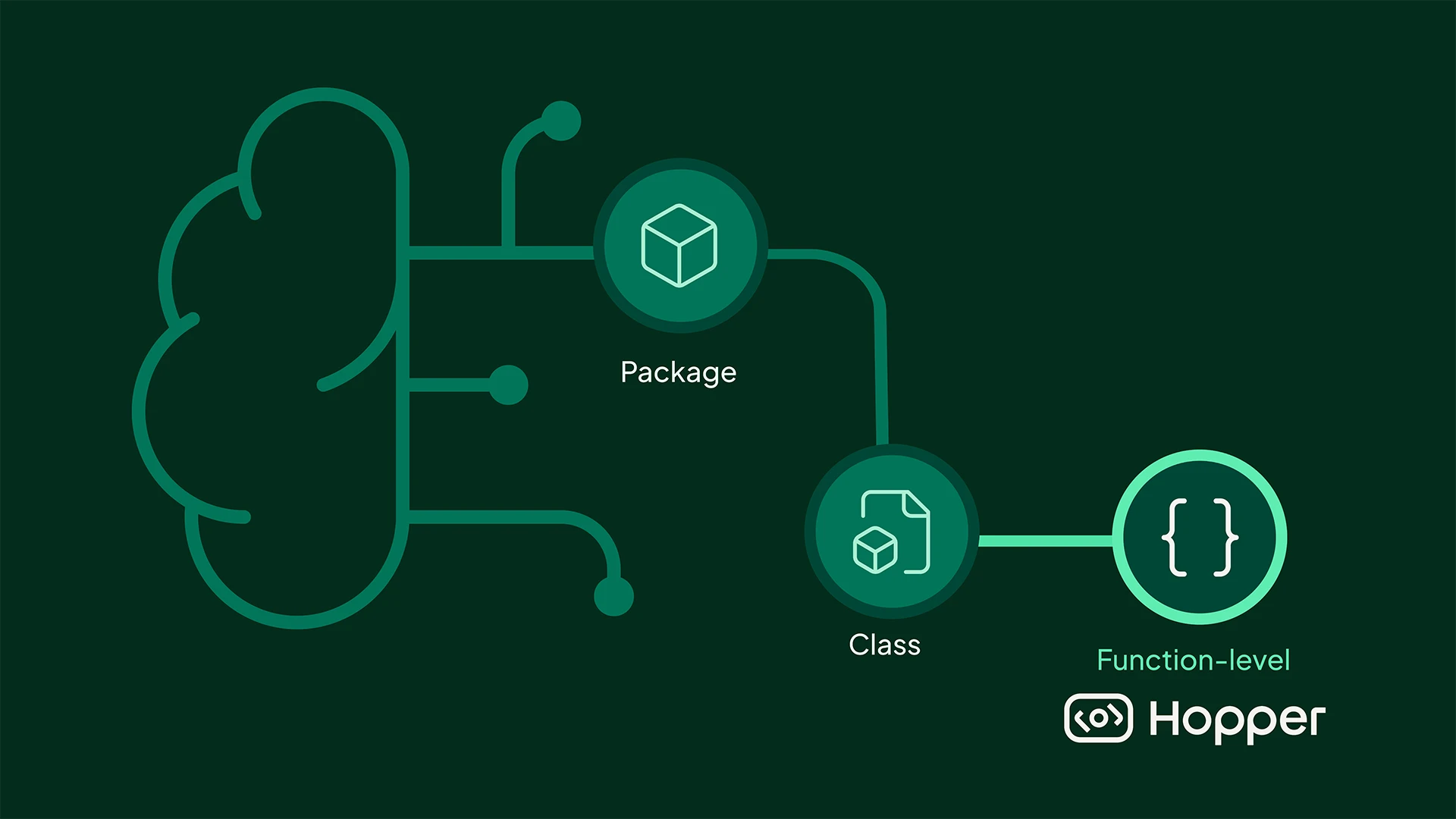

Good Vibes, Bad Code? Vibe Coding and How to Secure It with Hopper
AI coding assistants are speeding up development by generating open-source code on the fly. But with that speed comes risk. Unpack how vibe coding expands your attack surface and how Hopper helps you secure what actually matters, down to the function level.
Insights
Newsroom
Hopper Press Mentions and Releases
Visit Publication Article

September 15, 2025
In Praise of Resilience: Why We Invested in Hopper Security
-Logo.wine.png)
Visit Publication Article

September 4, 2025
The ART of Taming Agents: A CISO’s Framework for Managing Enterprise Risk in the Age of Agentic AI

Visit Publication Article

April 25, 2025
Hopper Uncovers Over 2.5 Million Vulnerabilities Hidden in Java

Visit Publication Article

April 22, 2025
Hopper raises $7.6M to accelerate software development with streamlined risk management
Visit Publication Article

April 22, 2025
Open Source Security Firm Hopper Emerges From Stealth With $7.6M in Funding

