Exploitability, Verified. Across Every Application.
Modern software lives everywhere: in container registries, code repositories, artifact registries, and cloud workloads. When a new vulnerability hits, teams need to know whether it affects them, whether it is exploitable, and how to remediate it across supported versions. Fixing what matters, and sometimes what must be patched regardless of exploitability, continues to demand significant time and engineering effort.
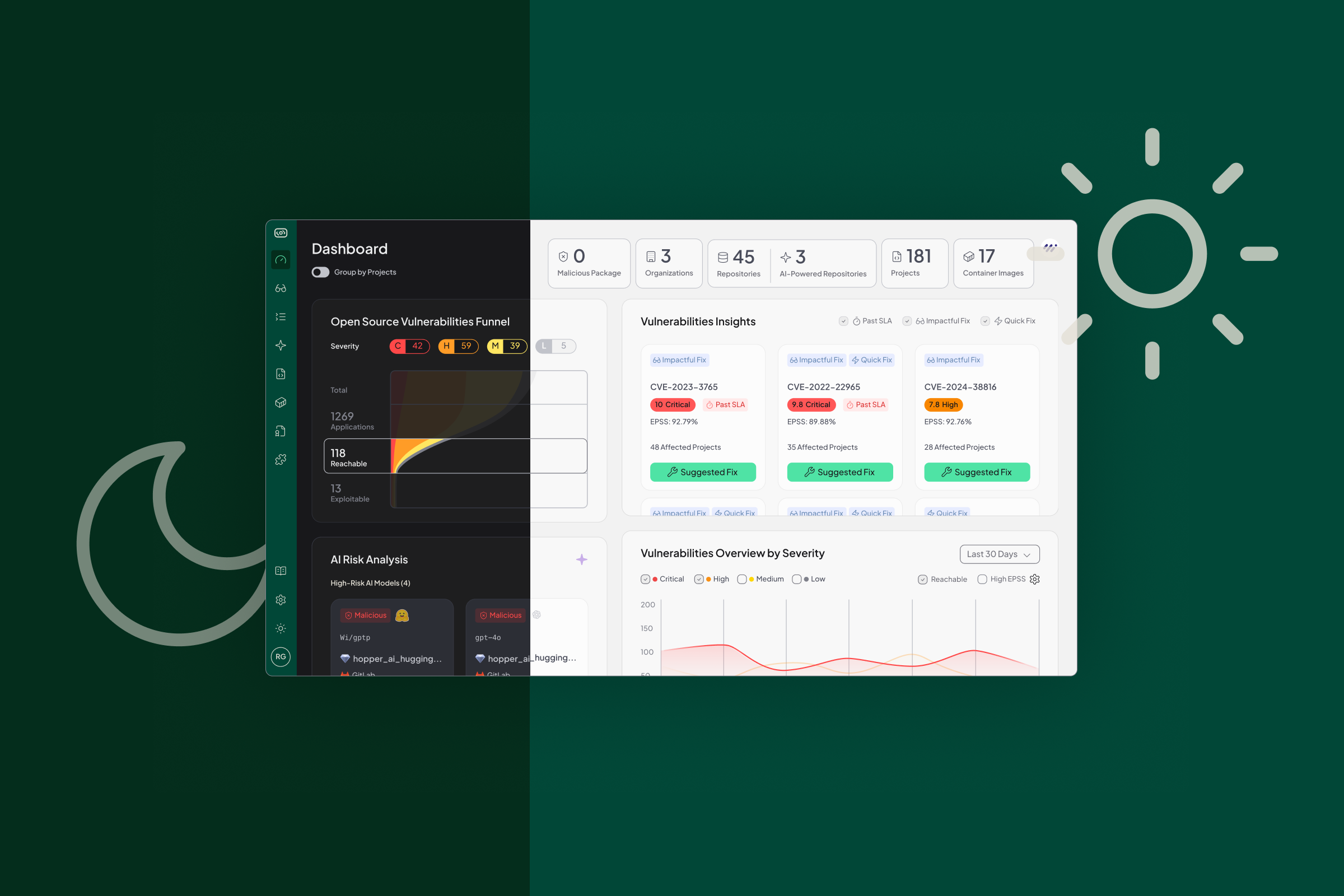
Today we are introducing Hopper Exploitability Verification, an AI-driven capability that confirms exploitability across every application your business builds, buys, or uses. Hopper delivers verified intelligence that accelerates response, reduces noise, and gives teams the confidence to act quickly and safely.
The Challenge: New Vulnerabilities Trigger Alerts, Not Answers
Security, product, and engineering teams are overwhelmed with vulnerability notifications across an increasingly distributed software ecosystem. The issue is not visibility. It is verification.
Most tools can tell you that a vulnerable component exists somewhere in your code or containers. But that is no longer enough. Teams need to:
- Verify exploitability in the context of their application
- Prioritize what must be fixed now versus what can be safely deferred
- Anticipate potential breaking changes introduced by remediation
- Assess the engineering cost of remediation and backporting
- Leverage generated or guided fixes to reduce manual remediation work
Without this information, teams are forced into manual investigation and guesswork. Triage slows. Ticket queues expand. Advisories are delayed. The backlog is never-ending. Engineering time is spent chasing or patching issues that never present real risk.
Modern teams do not need tools that simply tell them what is vulnerable.They need tools that validate impact and help deliver the fix.
Hopper replaces assumption with verified impact and AI-generated fixes, so organizations can resolve what matters and avoid unnecessary rework.
Hopper: Verified Intelligence For Vulnerability Response
Hopper determines real exploitability by combining a proprietary database of exploitable functions with advanced program analysis that understands how code behaves in practice. By tracing data flow, control flow, and framework entry points, Hopper provides its AI with the context needed to evaluate vulnerabilities against actual application logic and CVE prerequisites. This unified intelligence powers fast, verified insight across source, binaries, containers, and artifact registries, and a clear view of which issues demand attention and which can be safely deprioritized.
Hopper’s AI Exploitability Agent performs the same workflow a vulnerability researcher would: inspecting vulnerable functions, reviewing advisory intelligence, analyzing reachability and data flow from framework entry points, and attempting an automated proof-of-concept against reachable paths to verify whether exploitation is possible. All analysis occurs offline in a secure sandbox, without modifying code or touching any live systems. This provides deterministic, evidence-backed assessments so teams can create advisories faster, meet MTTR and SLA targets, and focus on confirmed, exploitable risk.
Teams use Hopper to:
- Confirm exploitability with function-level evidence
- Identify affected assets instantly when new vulnerabilities appear
- Accelerate triage and advisory workflows for PSIRT and product security
- Reduce noise by focusing only on confirmed, exploitable risk
- Guide safe backporting by applying version-appropriate security patches to older or frozen branches
- Improve MTTR and customer communication with verified impact
Hopper enables organizations to respond with proof, not probability.
How Exploitability Verification Works
1. Identify Affected Assets Instantly
Hopper finds vulnerable components across Git repositories, container registries, cloud workloads, and artifact registries. No agents. No operational overhead.
2. Investigate With Function-Level Analysis
Hopper maps vulnerability reachability at the function level, analyzing call paths, data flow from framework entry points, and how inputs move through the application.
3. Reason Over Impact Using AI Agents
Hopper’s AI analyzes the full context of the vulnerability by reviewing the security advisory, prerequisites, and conditions required for exploitation.
It performs safe exploit simulation, static reasoning, data-flow validation, and multi-path analysis across framework entry points to determine whether exploitation is possible and whether the vulnerable pattern can be triggered in real application flows.
4. Deliver Verified Evidence In Seconds
Teams receive deterministic, auditable results that explain exactly why a vulnerability is or is not exploitable, including code-level details and trace information.
This workflow becomes even clearer in practice.
Customer Outcome: From 88 Alerts to Zero Panic
A customer recently received an alert for a potential SQL injection vulnerability in Django (CVE-2025-64459). When Hopper scanned their application, the platform surfaced 88 instances of the vulnerability across their codebase.
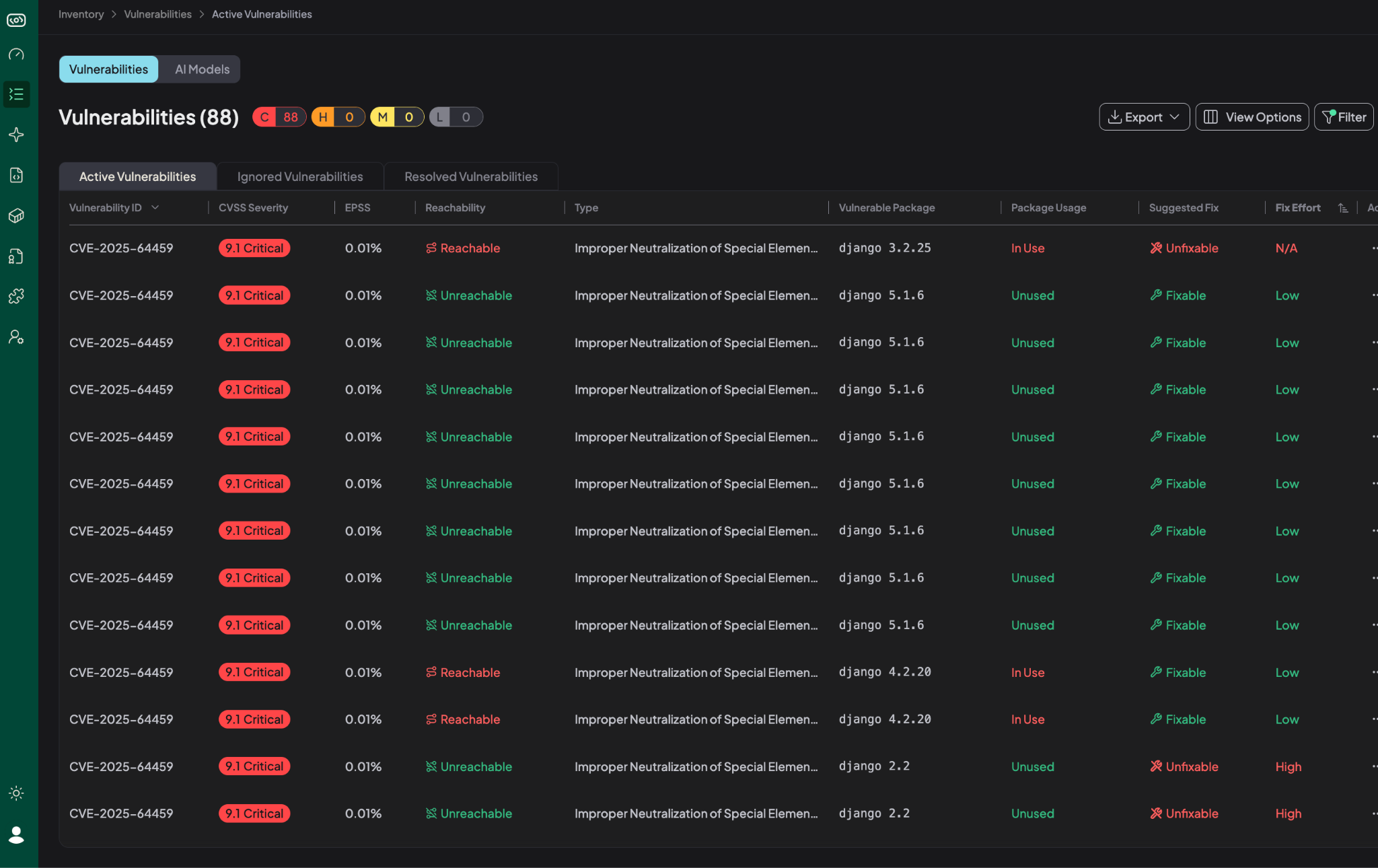
Hopper’s deeper analysis immediately refined the picture.
Based on Hopper’s function-level trace analysis, 7 of the 88 instances were reachable.
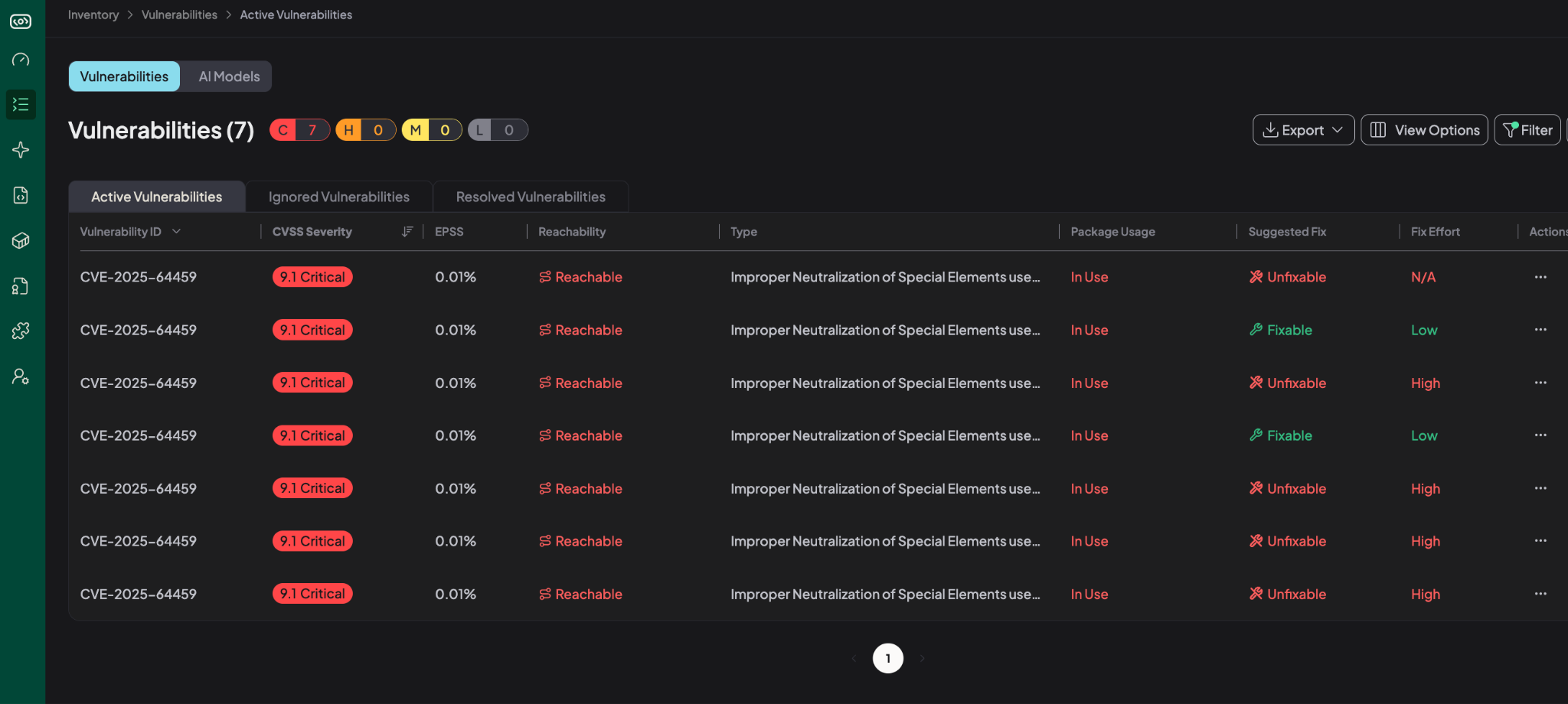
From there, Hopper’s AI Exploitability Agent automatically investigated each reachable path. The agent replicates the workflow of a vulnerability researcher and performs:
- Static inspection of each flagged function and surrounding logic
- Collection of advisory intelligence for CVE-2025-64459 and related Django guidance
- Framework-aware reachability and data-flow tracing from common Django entry points to determine user-input influence
- Automated proof-of-concept synthesis, attempting to construct requests and payloads required to trigger exploitation
- Offline sandbox evaluation, ensuring analysis remained isolated and safe
- Explicit reasoning, explaining why no valid exploit path existed
After completing its analysis, the agent determined that none of the 7 reachable instances were exploitable. Its final conclusion:
“The _connector parameter is never supplied from untrusted input, and there are no cases where a request-derived dictionary is expanded into Django query functions. No exploitable entry point exists. Confidence: high.”
Instead of launching a reactive patch cycle or diverting engineering time toward unnecessary remediation, the team received verified clarity in minutes. No emergency workload. No disruption. No wasted developer time.
Hopper took the team from 88 alerts to 0 exploitable in less than 3 minutes.
This is exploitability verification in practice: real impact confirmed, noise eliminated, and engineering energy preserved for what matters.
Why Exploitability Verification Matters
Vulnerabilities are growing nearly 100% year over year, and software now spans far more than source code. It lives in containers, binary artifacts, cloud workloads, package registries, and third-party components where new vulnerabilities may be discovered long after the software is released.
Teams need to understand vulnerability impact instantly across all of it. Not only during development. Not only inside the SDLC. Everywhere their software runs, ships, and scales.
Exploitability verification gives organizations the clarity to act with confidence:
Security and AppSec
- Validate exploitability across complex, distributed systems
- Reduce noise and manual investigation
- Meet MTTR and SLA commitments with verified evidence
PSIRT and Product Security
- Identify affected versions and products in seconds
- Accelerate advisory creation with confirmed impact
- Strengthen customer trust with transparent, evidence-backed communication
Engineering
- Avoid unnecessary remediation cycles
- Receive direct links to the affected code paths
- Patch safely with clear visibility into potential breaking changes
Operations
- Protect workloads across ECS, EKS, AKS, and hybrid environments
- Understand real impact on running systems
- Build consistent, repeatable workflows backed by AI reasoning
Exploitability verification aligns every team around a single source of truth: what is actually exploitable, and what needs to be fixed now.
AI That Actually Accelerates Security
Vulnerability response has always struggled with the same imbalance: too many alerts, not enough clarity. Hopper resolves this by combining AI reasoning with function-level evidence to verify what is truly exploitable and what can be safely ignored. The result is faster decisions, fewer distractions, and a workflow that keeps every team aligned on what matters most.
In an environment where complexity keeps growing and time keeps shrinking, Hopper gives organizations a simple advantage: the ability to move with confidence, not caution. Verified impact replaces assumption. Precision replaces noise. Action replaces delay.
Noise kills speed. Hopper turns noise into knowledge.