The Enterprise Platform for Impactful,
Evidence-Based AppSec
Tired of drowning in false positives and endless security alerts? Hopper redefines open-source security with 93% noise reduction, function-level reachability, and 4x fewer false positives than other reachability vendors. Experience greater accuracy with web app frameworks (Java Spring, Django)—all with agentless, 5-minute deployment.
Trusted by Leading Software Teams
















Hopper Use Cases

Noise-Free, Evidence-Based SCA
- Identify function-level reachable vulnerabilities
- Eliminate 93% of security noise
- Evidence-based findings developers trust, including root cause analysis, call graphs, and direct links to your source code

AI AppSec Suite
- Detect vulnerable AI-generated code and model risks with AI-BOMs, file-level mapping, and insecure behavior detection
- Accelerate fixes with intelligent, AI remediation guidance
- Automate triage, prioritization, and policy enforcement across your workflows

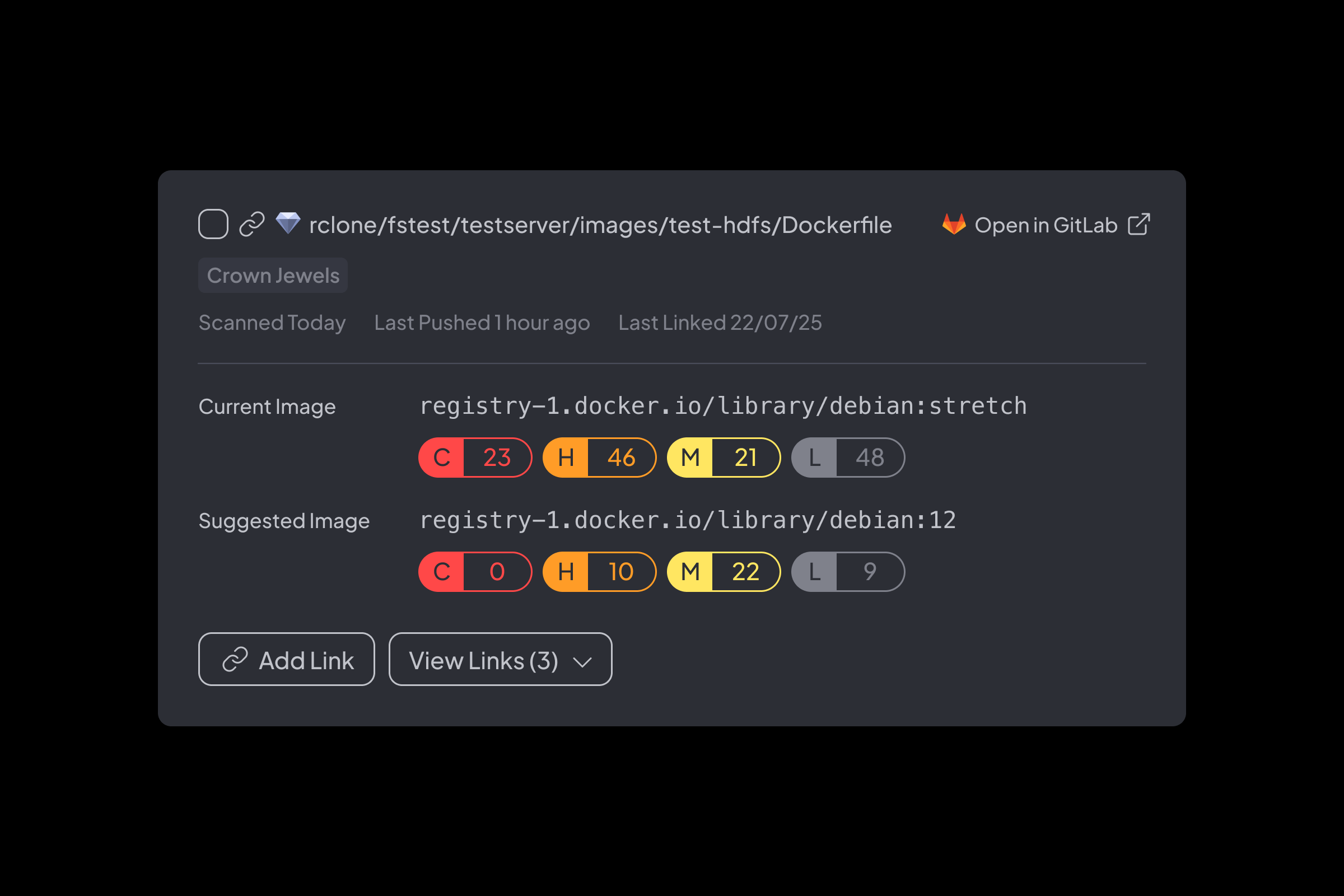
Container Scanning
- Scan images for vulnerable packages used by active services
- Trace each vulnerability from source code to base image to the final container image, and the service it impacts
- Continuous observability without agents or CI/CD modifications

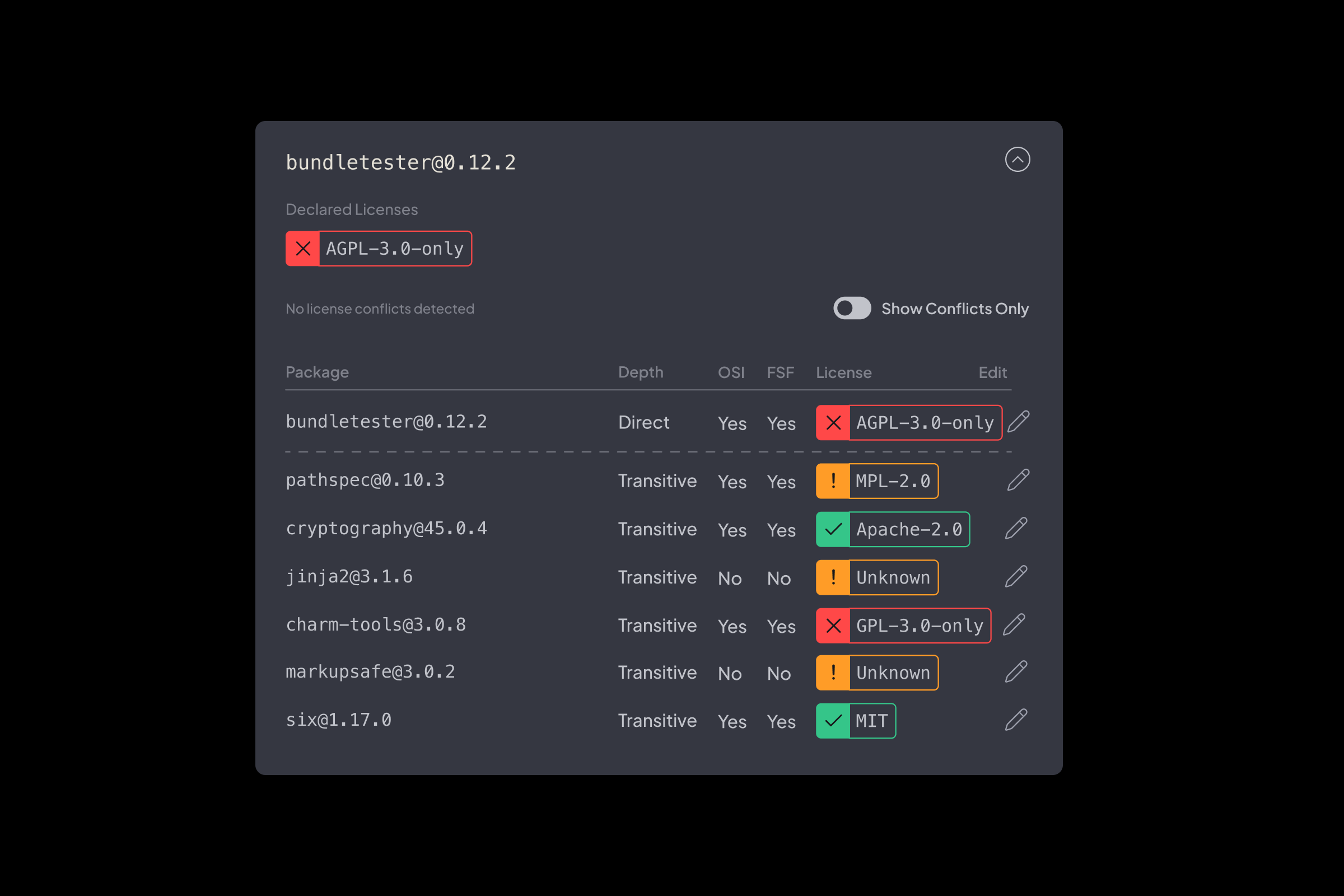
License Scanning
- Automatic Asset Discovery: Detects new projects and applications in real-time.
- Build Without CI/CD Deployment: Test security impacts before deployment.
- Advanced Runtime Simulation: Reproduce real-world execution conditions for deeper insights.

Remediation and Insights
- Identify and remediate high-impact issues across multiple projects with a targeted fix
- Track SLA adherence, MTTR, and fix velocity with performance insights
- Deliver personalized, actionable remediation plans including quick fixes
What Makes Hopper Better
10X Noise Reduction with Reachability
Reachability down to the function-level, across direct and transitive dependencies
Filters out 93% of false-positive alerts
Maps findings to the exact file and line of code for fast remediation
Function-Level Reachability Analysis
Evidence-backed, actionable remediation developers trust
Root cause tracing to files and functions
Fix effort estimates and guided call-graph-based remediation
Streamlined Remediation Flows
Agentless, five-minute onboarding
Supports containers, serverless, client-side, on-prem, and cloud
Git to containers to AI-generated code
Built for Enterprise AppSec

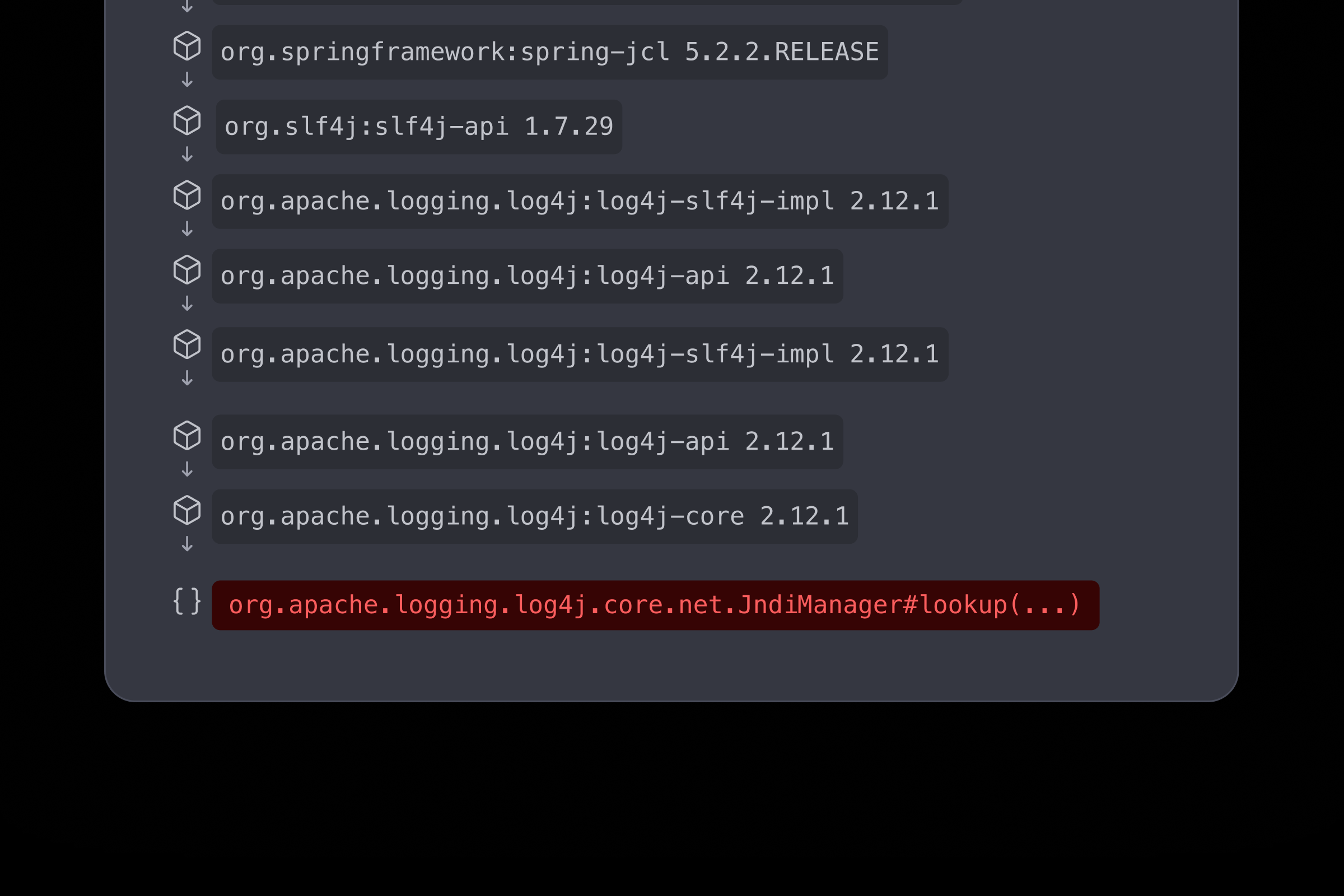
Function-Level Reachability
Go beyond package- or class-level detection by simulating application behavior to trace if and how the vulnerable function is actually invoked.
Teams focus only on reachable risks, reduce wasted remediation effort, and earn developer trust with precise, evidence-backed findings they can verify and act on.

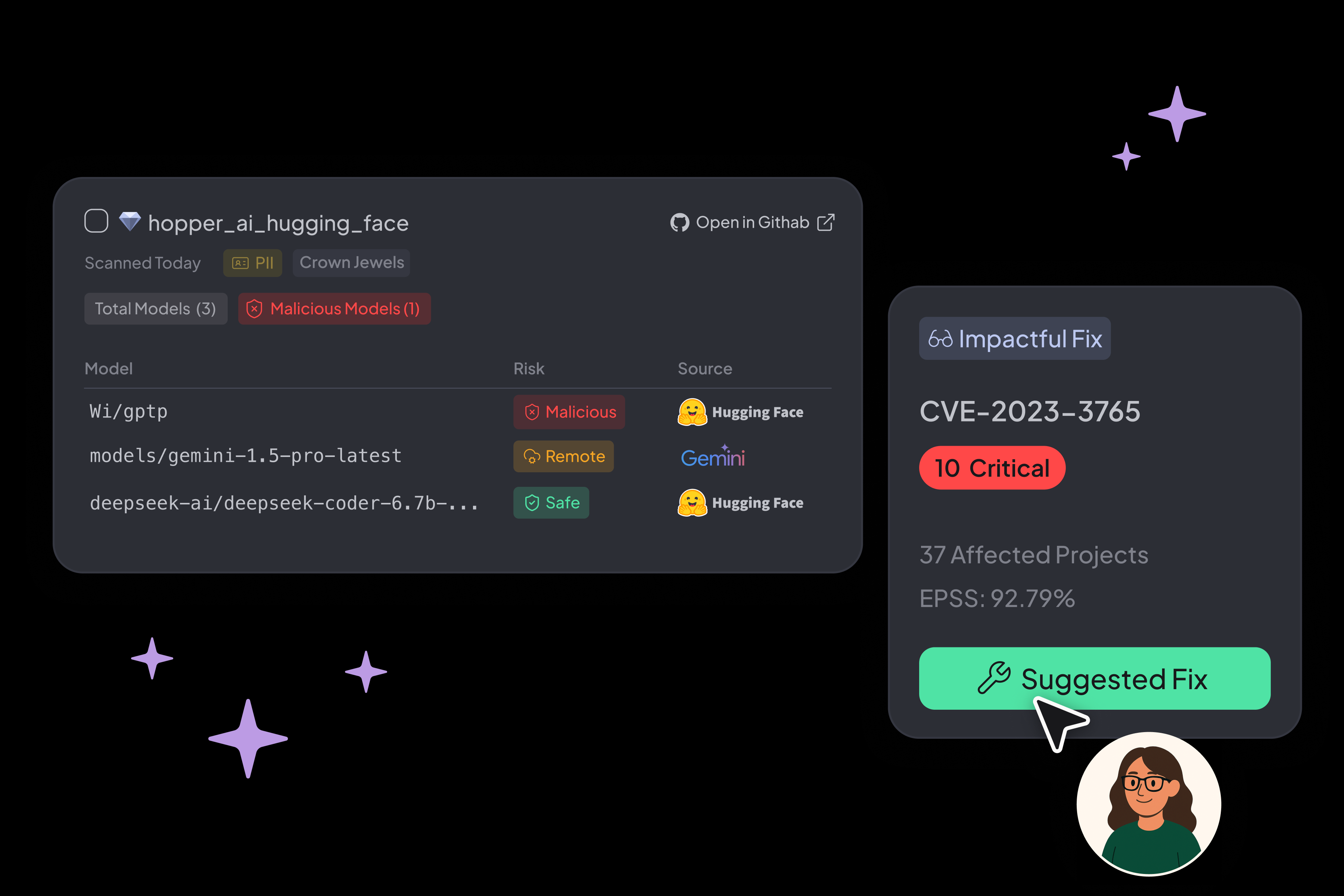
See Every Model, Secure Every Risk
Generate AI-BOMs, surface embedded or externally connected models, and detect malicious behavior like insecure deserialization patterns (pickle). Hopper provides policy-violating model use with evidence-backed root cause insights.
Gain visibility into AI model usage and risks across applications, enabling faster, more accurate decisions without manual code review.

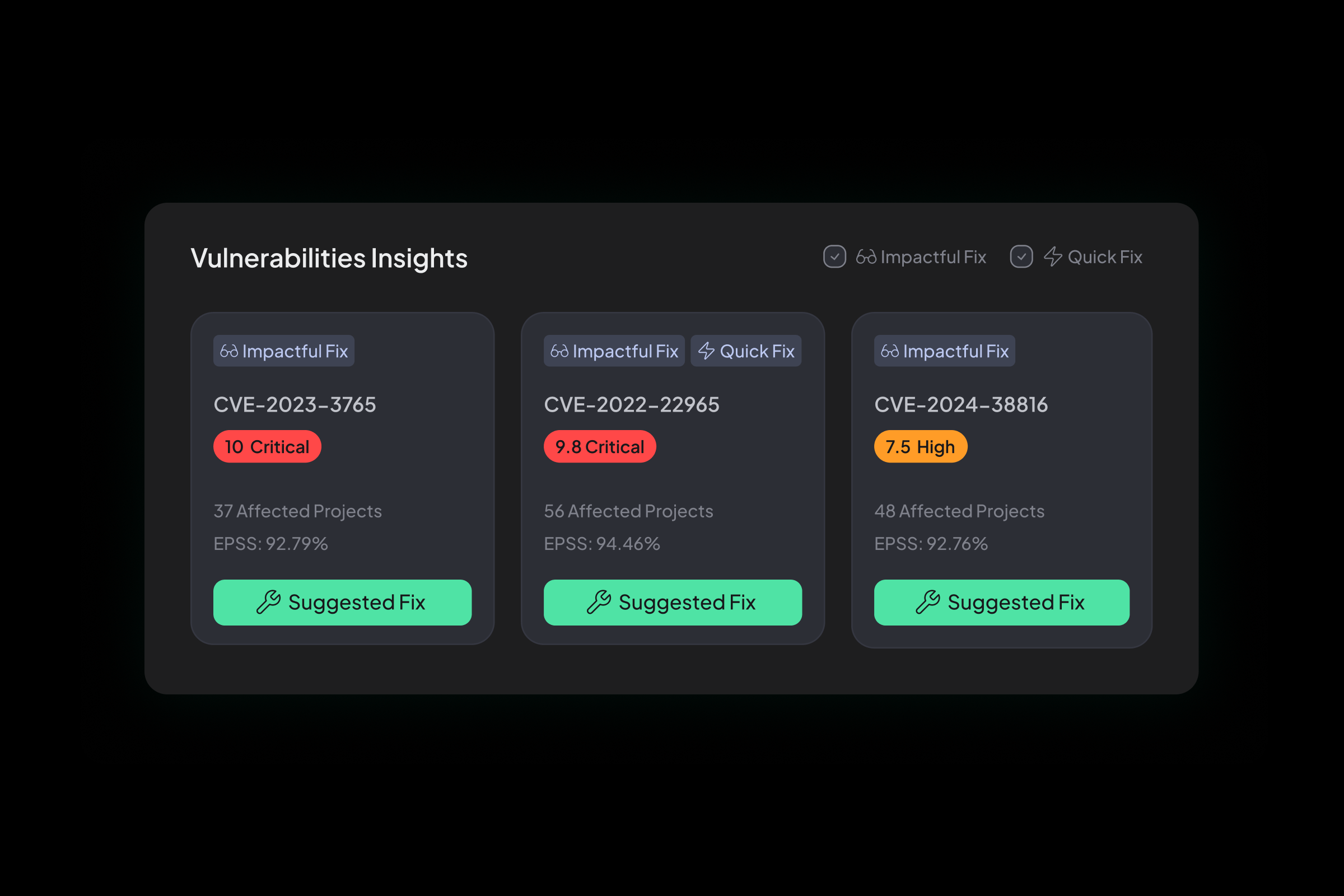
Cross-Project Vulnerability Insights
Identify shared vulnerabilities across projects, repositories, services, and applications. Hopper surfaces the root cause, deduplicates alerts, and the highest-impact fixes, pinpointing where a single remediation effort can eliminate risk across multiple systems.
Avoid duplicate alerts and manual triage by zeroing in on the origin of issues, enabling broader security impact with fewer fixes and less effort.

Deep Asset and Dependency Intelligence
Automatically discover new repositories and segment active applications from idle projects. Hopper detects hidden or shaded dependencies, such as repackaged or renamed libraries, that other tools miss. This ensures complete visibility across your software supply chain.
Eliminate blind spots by uncovering obscure components and focusing security efforts where they matter most.