From Container Image to Fix, Without the Overhead
Hopper analyzes containers with reachability-based precision to detect vulnerabilities that actually impact your applications. It scans images from your registry, maps issues back to your source code, and recommends safer alternatives. No agents, CI changes, or DevOps involvement.

No Video Found
Why Hopper is Better
Find risks that actually impact running containers
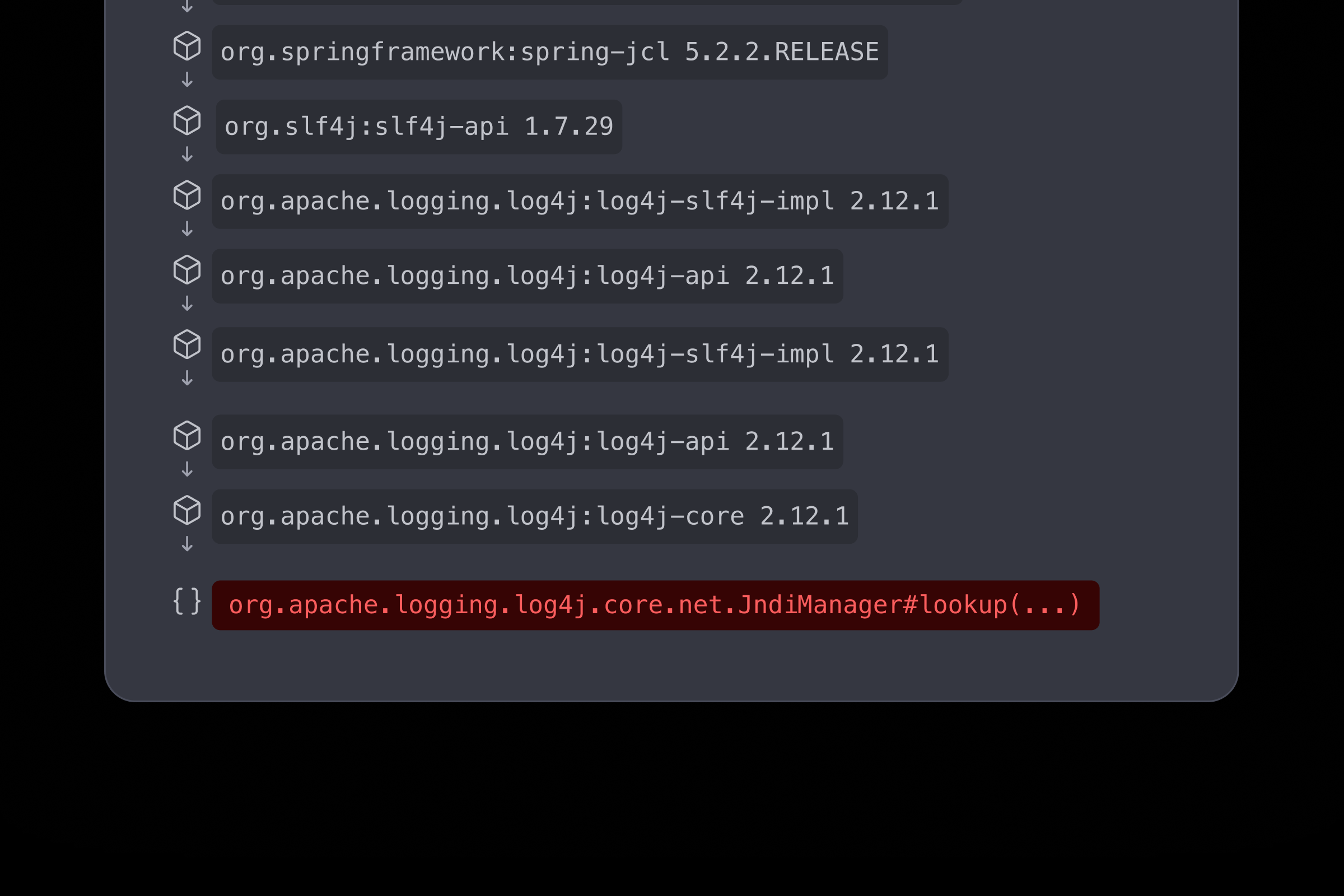
Surface only the risks that are reachable from application code, not everything in the image.
Connect container issues back to source
Trace vulnerabilities seamlessly from containerized services to Dockerfiles and source code repositories for fast and precise remediation.
Deploy without operational friction
Scan containers directly from your registry with no agents, runtime hooks, or CI configuration required.
Built for Enterprise AppSec
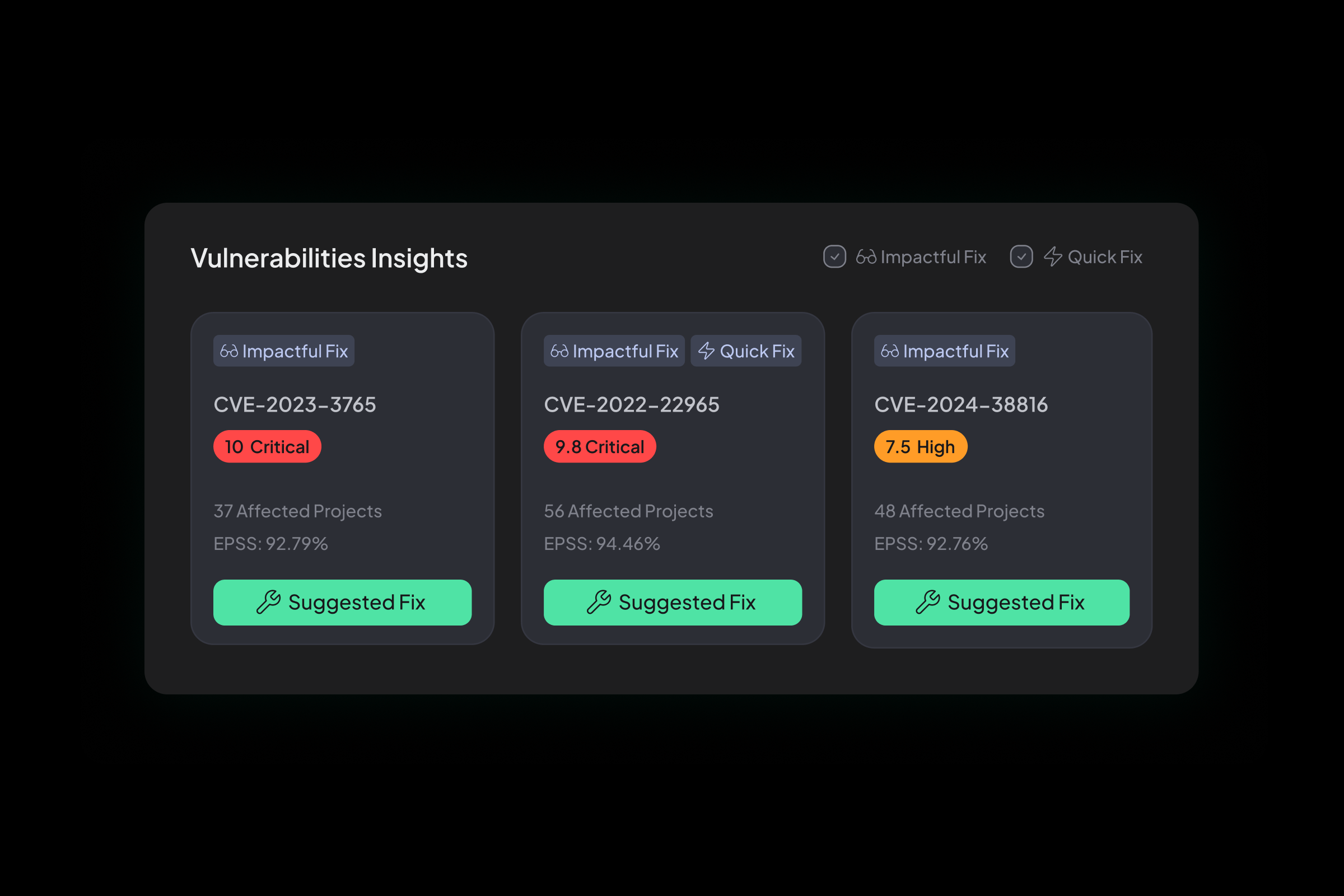
Reachability-Aware Image Scanning
Analyzes container images to identify which vulnerabilities are reachable by the services that use them.
Why It Matters:
Helps teams focus on real risk and avoid unnecessary patching.


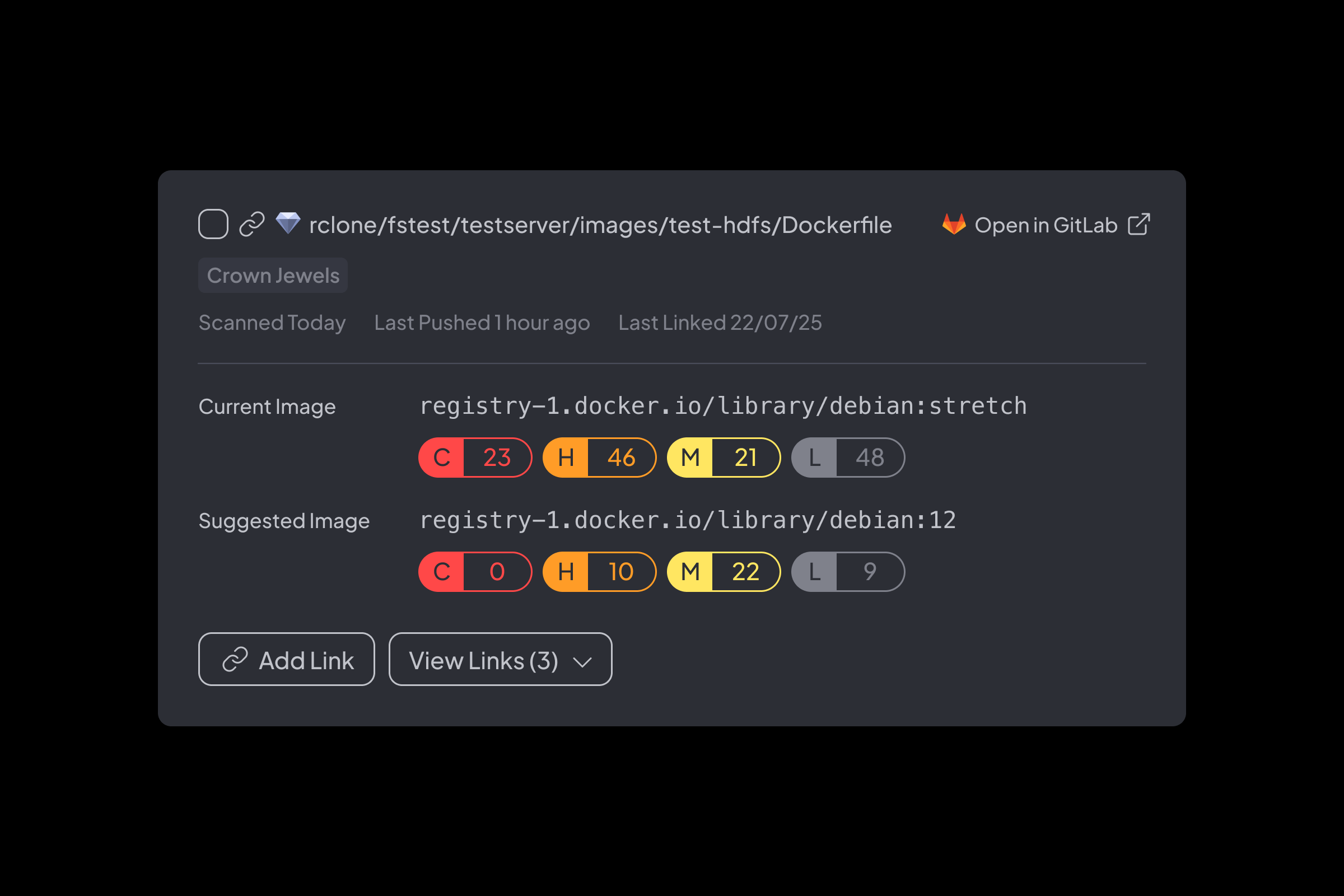
Safer Image Suggestions
Compares your current image to safer, compatible alternatives and recommends upgrades that reduce vulnerabilities.
Why It Matters:
Reduces exposure without breaking builds or adding research overhead.
We have much less friction with DevOps and our developers, and we reduced our backlog of open tickets by 70% with Hopper.

SCM-Linked Vulnerability Mapping
Connects vulnerabilities to the exact repo, Dockerfile, or service where the image originated.
Why It Matters:
Developers get full traceability from risk to fix with no manual effort.

Hopper Use Cases

Noise-Free, Evidence-Based SCA
- Identify function-level reachable vulnerabilities
- Eliminate 93% of security noise
- Evidence-based findings developers trust, including root cause analysis, call graphs, and direct links to your source code

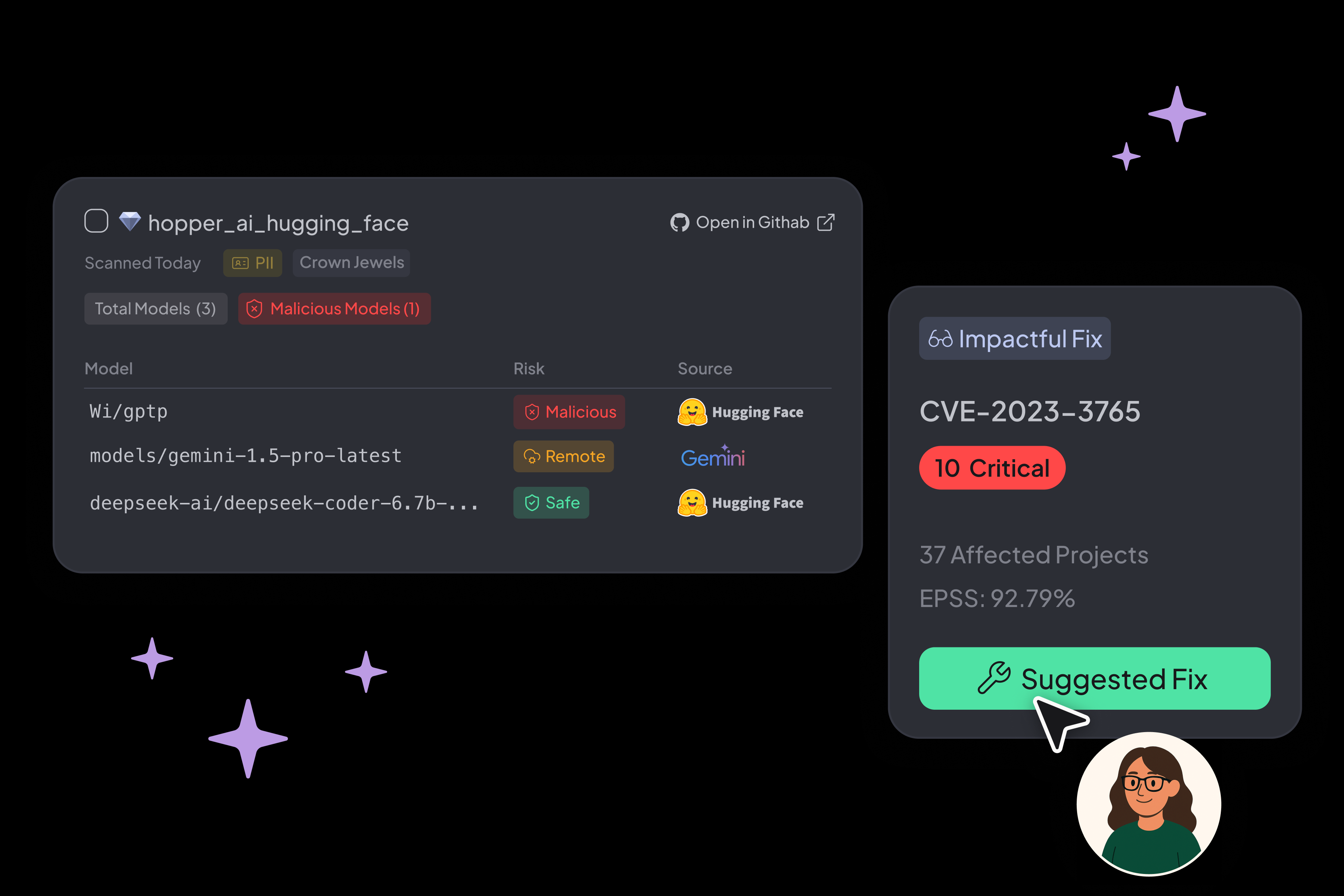
AI AppSec Suite
- Detect vulnerable AI-generated code and model risks with AI-BOMs, file-level mapping, and insecure behavior detection
- Accelerate fixes with intelligent, AI remediation guidance
- Automate triage, prioritization, and policy enforcement across your workflows

Container Scanning
- Scan images for vulnerable packages used by active services
- Trace each vulnerability from source code to base image to the final container image, and the service it impacts
- Continuous observability without agents or CI/CD modifications

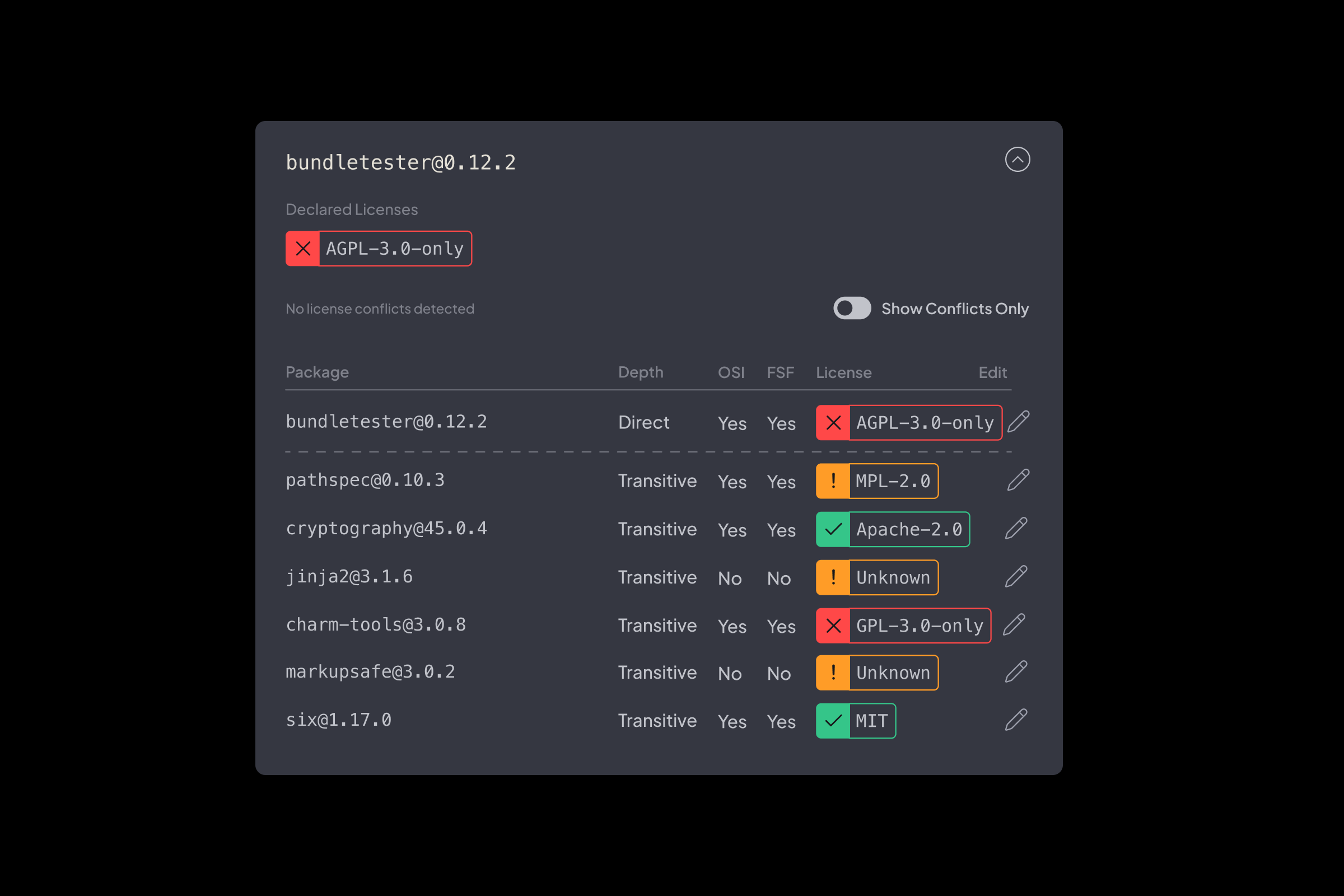
License Scanning
- Automatic Asset Discovery: Detects new projects and applications in real-time.
- Build Without CI/CD Deployment: Test security impacts before deployment.
- Advanced Runtime Simulation: Reproduce real-world execution conditions for deeper insights.

Remediation and Insights
- Identify and remediate high-impact issues across multiple projects with a targeted fix
- Track SLA adherence, MTTR, and fix velocity with performance insights
- Deliver personalized, actionable remediation plans including quick fixes