The Hidden Cost of AppSec Noise
Every security team knows the feeling: dashboards lighting up with thousands of new CVEs, tickets flooding into Jira, and a growing backlog that no one can ever quite get ahead of.
It is the background hum of modern AppSec: a constant signal that feels like progress but hides a deeper problem. Each alert, each ticket, and each "potential" vulnerability costs time and money to process. The real question is: how much of that work actually reduces risk?
When we measured it, the numbers were brutal.
Across organizations, the fully loaded cost of handling a single vulnerability from alert to closure averages nearly $1,000. Multiply that by thousands or tens of thousands of issues generated each year, and it becomes clear: AppSec teams are paying a vulnerability noise tax on every false positive, every low-impact CVE, and every alert that never touches production code.
Even when teams decide not to fix an issue, they still pay part of that cost. Review, validation, and deprioritization consume hours of triage time, adding to a backlog that grows faster than it can be resolved. The result is a constant tradeoff: fix what you can, accept the rest, and carry the operational debt of known risk that keeps accumulating.
Breaking Down the $967.50 Ticket
To understand the scale of waste, let’s look at the real process behind one vulnerability ticket. [We also validate this breakdown with our customers. If your experience differs significantly, we would love to learn from it!]
Total: $967.50 and 12.75 hours per vulnerability.
The Economics of Inefficiency
Every dollar spent triaging non-reachable or non-exploitable vulnerabilities is a dollar not spent reducing real risk or building the business. It’s time that could go toward fixing bugs, improving the product, or developing new revenue-generating features. It also creates frustration and dissatisfaction among both engineers and AppSec teams, who see time and talent wasted on noise instead of progress.
AppSec leaders operate within tight budgets, often competing for the same headcount as engineering or IT. Yet a significant portion of that budget is consumed by manual work generated by noisy tools.
Traditional Software Composition Analysis (SCA) solutions flood teams with findings on every vulnerable package, regardless of whether it is ever executed. The result is predictable: developers spend hours validating irrelevant issues, and security teams spend weeks reconciling the same false positives across systems.
This is not just a productivity issue. It is a structural economic problem.
While organizations face more than 30,000 new CVEs each year (40,009 in 2024 alone, according to the National Vulnerability Database), most create internal tickets for only a subset of those. If your team opens around 10,000 tickets in a year, the cost burden quickly adds up.
At nearly $1,000 per ticket, a mid-sized enterprise can spend close to $10 million each year in engineering and security time, much of it on issues that are never exploitable. Scale that across a global enterprise with hundreds of applications and thousands of repositories, and the waste begins to rival the cost of the tools themselves.
-1.png)
A Tax on Innovation
The vulnerability noise tax does not only drain budgets. It steals innovation time.
Developers lose trust in security findings when 90% of alerts turn out to be irrelevant. Engineers begin to tune out notifications, delay remediation, and deprioritize AppSec requests. Meanwhile, security teams lose credibility with leadership, forced to justify inflated ticket counts with limited impact.
It is a vicious cycle:
- More alerts lead to more noise.
- More noise leads to more fatigue.
- Fatigue leads to slower remediation and higher exposure.
And the longer the cycle continues, the more expensive it becomes.
What started as an efficiency gap turns into a business risk. Teams spend more time managing processes than managing exposure, and risk accumulates silently while budgets are burned on noise.
Why Traditional Approaches Fail
Most AppSec tooling was built on a simple assumption: if a package is vulnerable, it is risky. But in practice, the vast majority of vulnerabilities are never invoked in the application’s actual execution path.
Static SCA tools, dependency scanners, and even some runtime monitors cannot distinguish between theoretical and real risk. They surface every CVE tied to every package, leaving security teams to do the heavy lifting of validation.
This reactive model scales poorly. As organizations adopt more open source, containerized environments, and AI-generated code, the number of dependencies explodes, and with it, the alert volume.
Without precision, scale becomes noise. And noise becomes cost.
Cutting the Noise Before It Hits Engineering
At Hopper Security, we believe AppSec does not have to be this way.
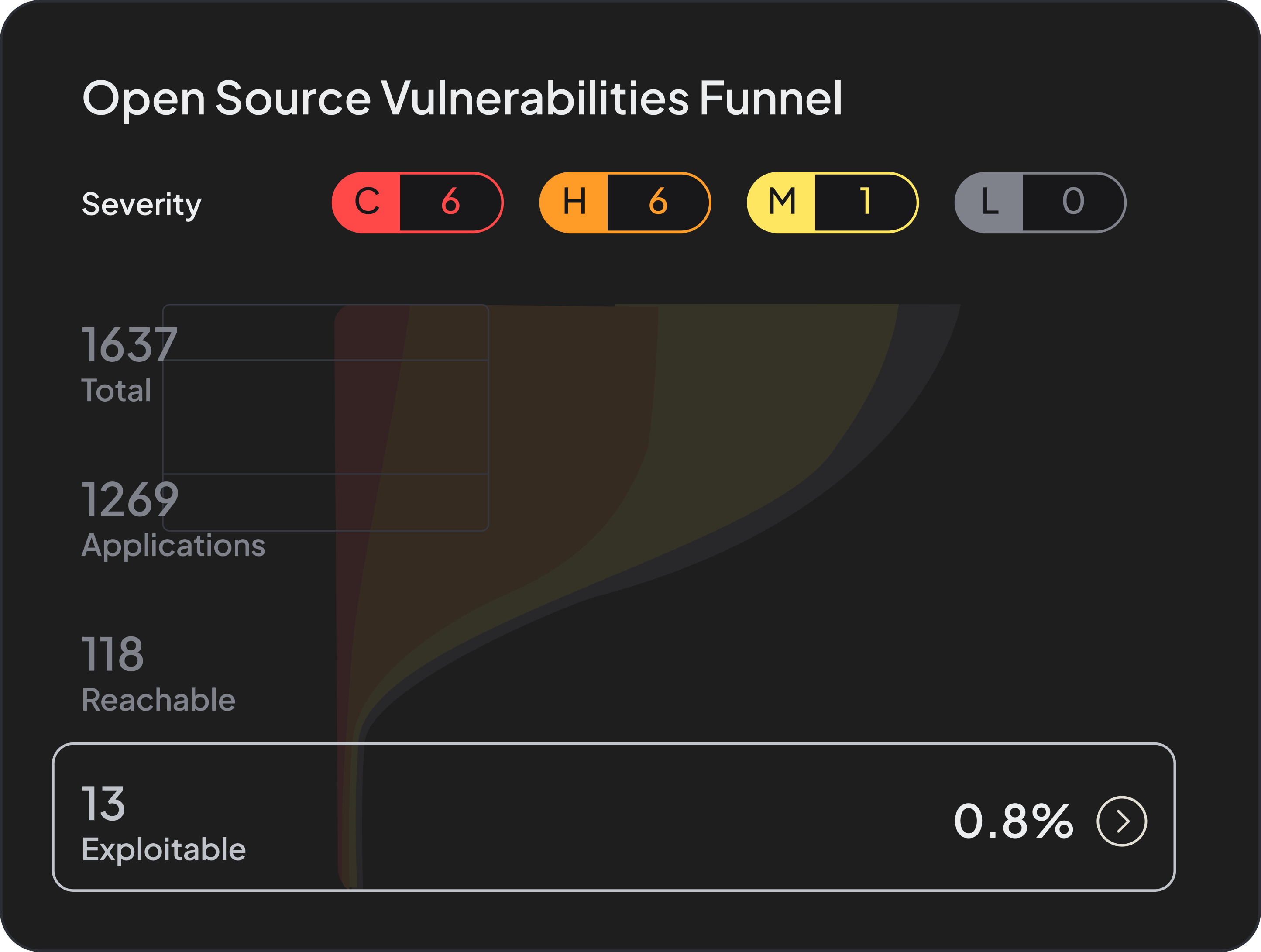
Our function-level reachability analysis changes the economics of vulnerability management by cutting 93% of non-reachable findings before they ever reach a developer’s queue. The cuts deepen when organizations apply risk-based filters such as EPSS scores, exploit maturity, or business-critical asset tagging.
By combining reachability with contextual risk factors, teams can reduce false positives even further and focus only on vulnerabilities that are both reachable and likely to be exploited. This layered approach ensures that engineering effort aligns with true exposure, not theoretical risk. In practice, this level of precision typically leaves customers with only 0.1% to 1.5% of original findings.
The result is a security process that focuses effort where it counts:
- Security teams spend less time triaging.
- Developers see fewer tickets, each backed by concrete evidence including root cause analysis, call graphs and fix effort estimates.
- Executives can finally connect AppSec investments to measurable business impact.
It is not about scanning more. It is about knowing more.
From Noise Tax to Security Dividend
When you eliminate the vulnerability noise tax, you unlock something bigger than cost savings: capacity.
Function-level reachability gives back time to the people who make the business move. Those reclaimed hours can fund new features, security improvements, or innovation initiatives that would otherwise be deferred.
It is the difference between security as overhead and security as enabler.
Teams that adopt reachability analysis report immediate results: fewer false positives, faster mean time to remediation, and better collaboration between security and engineering. But the long-term benefit is cultural: a shift from "security versus speed" to "security as precision."
The Budget Reality
AppSec budgets are not growing. In most organizations, they are flat, even as the attack surface expands. Leaders are being asked to do more with the same headcount, the same tools, and the same hours in the day.
Corporate budgets today are divided between people and platforms. Security teams are expected to justify every dollar, whether it goes toward renewing a tool, hiring another engineer, or improving developer productivity. Each decision is judged by measurable return on investment.
Cutting noise is no longer a matter of operational efficiency. It is a fiscal necessity.
If your team is spending 60-80% of its AppSec budget triaging false positives, the math does not work.Those costs fall directly into the people category: hours spent investigating issues that never translate into real risk reduction.
At the same time, the tooling side of the budget is under greater scrutiny. Leaders need to prove that every platform directly supports measurable outcomes such as reduced MTTR, lower vulnerability counts, and improved audit readiness.
The future of secure development depends on precision; on proving what is reachable and exploitable, not just what is present.
Function-level reachability gives teams that precision. It transforms AppSec from a cost center into a performance-driven program by filtering noise before it consumes budgeted hours and by proving which vulnerabilities truly matter. It allows teams to show boards and auditors that they are prioritizing real, provable risk instead of chasing theoretical vulnerabilities.
Precision is not only a technical advantage. It is a budgeting strategy that keeps AppSec sustainable in an environment where every hour and every tool must show its value.
End the Tax. Invest in What Matters.
The vulnerability noise tax is real, measurable, and solvable. Every ticket that does not lead to real risk reduction is money burned.
It is time to stop accepting inefficiency as the cost of doing business.
Security should be a multiplier, not a tax. See how Hopper eliminates the noise tax in your environment.