Introduction
In early 2025, a Fortune 500 enterprise undertook an initiative with Hopper to modernize its open-source vulnerability management approach. Facing growing volumes of security alerts from traditional SCA tools, the company sought a more precise method to detect, prioritize, and remediate real risks that impact business-critical applications.
Challenges Faced
The company's existing security stack generated tens of millions of alerts, 10,000 of which originated from just over 80 applications selected for initial analysis. This overwhelming volume made it nearly impossible to separate meaningful threats from background noise. The incumbent tools struggled to detect issues in internally developed libraries and lacked the function-level precision needed for effective prioritization. As a result, policy waivers became a common workaround, allowing potentially exploitable vulnerabilities to persist in production.
This inefficiency carried a broader cost. Internal assessments revealed that 5–7% of total R&D time was being spent on fixing security issues, most of which stemmed from low-priority SCA alerts. This burden was largely driven by strict internal SLAs and MTTR policies typical of the finance industry, where teams are required to remediate vulnerabilities regardless of their actual exploitability. Reducing this overhead was essential not only for improving security outcomes, but also to meet a key organizational KPI: decreasing vulnerability noise to boost engineering velocity across the company.
Solution Implemented
Deployment and Integration
To address these challenges, the company deployed Hopper in its on-premise environment. Hopper was configured to analyze both Java, including Spring, and Python codebases, aligning with the company’s standard development stack. Integration was seamless with existing systems, including GitHub (self-hosted) and JFrog, enabling full visibility across the software supply chain.
Function-Level Reachability and Risk Enrichment
Hopper began by scanning repositories and generating a detailed reachability map of vulnerabilities across the software supply chain. Its core innovation lies in performing deep, function-level reachability analysis to determine whether vulnerabilities are actually accessible from real application logic. These findings are then enriched with threat intelligence data, including Exploit Prediction Scoring System (EPSS) ratings and CISA’s Known Exploited Vulnerabilities (KEV) catalog, to help teams prioritize based on real-world risk rather than theoretical exposure. These signals are not used as gating criteria, but as inputs to guide prioritization based on actual risk.
This precision allowed the security team to eliminate non-actionable noise and focus remediation efforts on a narrow set of vulnerabilities that were both reachable from real application logic and highly likely to be exploited. Hopper’s ability to combine function-level reachability with contextual enrichment enabled accurate, high-confidence prioritization at scale.
Internal Libraries and Hidden Risk
Beyond external dependencies, Hopper surfaced extensive risk in the company’s internally developed libraries. These libraries, stored and distributed through internal artifact repositories like JFrog, are often overlooked by traditional tools. While platform teams had patched the latest versions, older vulnerable versions remained in circulation and were silently pulled into builds. This created a dangerous false sense of security: repositories appeared clean, SCA scans passed, and yet vulnerable code persisted in production.
This visibility gap caused significant confusion. When runtime or container scanning tools flagged real vulnerabilities, engineers were unable to reconcile the alerts with clean artifacts and successful SCA checks. Lacking usage insight, teams frequently dismissed these as false positives, even though the risk was genuine. Hopper closed this loop by mapping internal libraries, identifying all versions in use, and tracing vulnerable call paths back to the source. This gave teams clear visibility into where outdated packages were still being pulled into production.
In total, 64.16% of all function-level reachable critical and high-severity vulnerabilities originated from internal libraries. These were not obscure or legacy components; they were foundational packages reused across the organization, amplifying the scale and urgency of the risk. For more on how internal libraries represent one of the most overlooked attack surfaces and how Hopper addresses it, see our write-up here.
Shaded and Transitive Dependency Detection
Hopper’s shaded dependency analysis further revealed hidden risks in transitive packages that were not explicitly declared but still loaded at runtime. These hidden dependencies, which traditional scanners typically miss, often carried critical vulnerabilities. In fact, nearly 33% of vulnerabilities identified during the initial analysis were found in shaded or otherwise hidden components. Hopper's ability to uncover these risks provided the team with greater confidence in the completeness of their security coverage.
Benchmarking Against the Incumbent Tool
To validate effectiveness, the company benchmarked Hopper against its incumbent tool across three selected applications. In every case, Hopper surfaced high-priority vulnerabilities that the existing solution failed to detect. Most notably, Hopper identified two vulnerabilities from the CISA KEV list, both exploitable and functionally reachable, that had gone completely undetected by the incumbent tool. These were not low-risk edge cases, but high-impact false negatives that posed real business risk and had already been actively exploited in the wild. Hopper’s ability to catch what others missed exposed a critical blind spot in the organization’s prior tooling and underscored the need for precision-driven analysis.
Accelerated Triage and Remediation
By visualizing full call graphs, Hopper enabled developers to trace the exact execution path from source code to vulnerable function. This clarity dramatically improved triage and allowed for faster, more targeted fixes with minimal business disruption.
Results Achieved
By deploying Hopper, the company achieved the following outcomes:
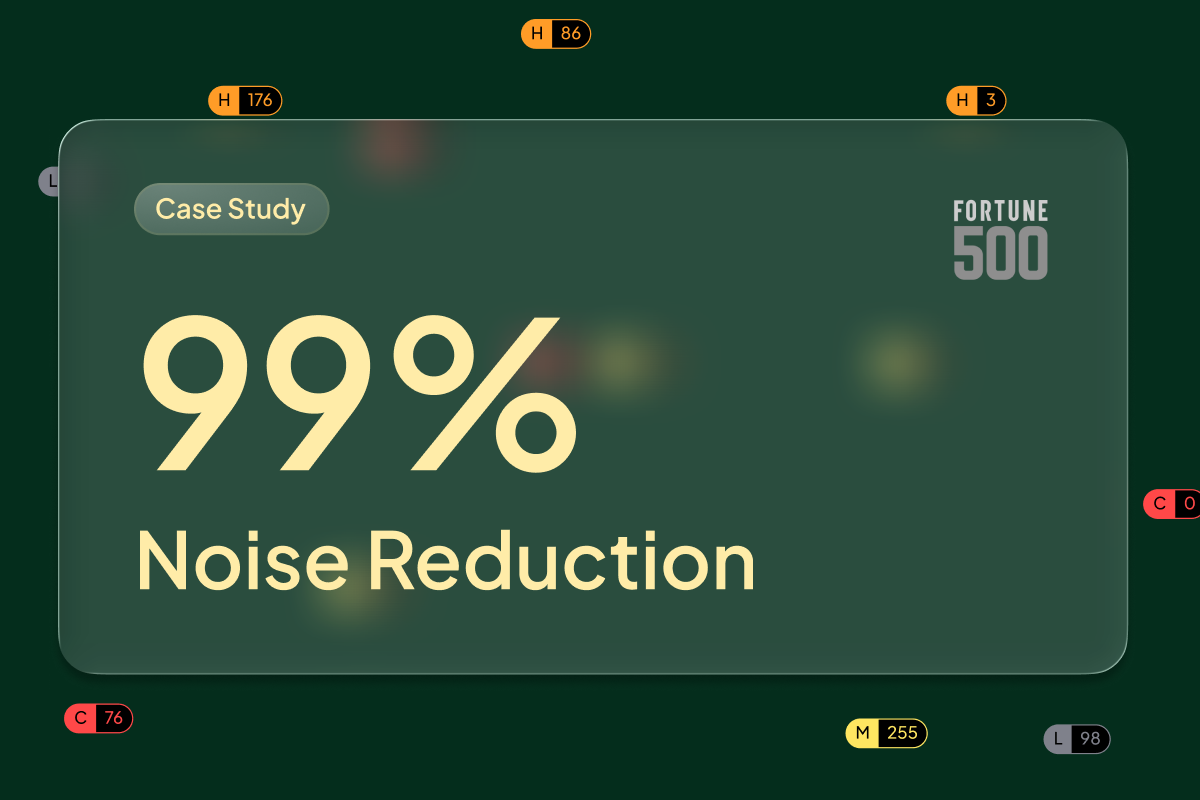
- Noise Reduction: Hopper reduced vulnerability volume from 9,500 down to 782 that were function-level reachable, and just 42 that were both exploitable and reachable, representing a 99.56% reduction in noise.
- KEV Detection: Identified two vulnerabilities listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog, both functionally reachable and missed by the incumbent tool.
- Internal Library Risk: More than 60% of critical and high vulnerabilities originated from internal infrastructure components, exposing a key blind spot in legacy scanning tools.
- Broader Detection: Hopper also surfaced critical risks previously waived via policy exceptions or undetected entirely by the incumbent solution.
- Faster Remediation: The function-level call graphs enabled developers to quickly trace and fix root causes, significantly accelerating mean time to resolution (MTTR).
Conclusion
This Fortune 500 enterprise now has a clearer, faster path to remediation with Hopper’s targeted insights. By eliminating noise and exposing real risk, including hidden threats in internal libraries, Hopper equipped both security and engineering teams with actionable data to improve response times, reduce cross-team friction, and elevate the company’s overall security posture.