Patches Don’t Equal Protection
We see this constantly. Clean, patched repositories. Yet builds are still vulnerable.
Why? Because older versions of internal libraries continue to live in artifact repositories and get silently pulled into applications. Developers patch a library and assume the job is done. The artifact system shows a clean version. The SCA tool reports no issues. Everything looks fine.
But in reality, vulnerable versions are still being used. They sit in the artifact store, defined in manifests, and make their way into production unnoticed.
This creates a false sense of security. Without visibility into what is actually being pulled into builds, teams are operating blind.
Risk Where You Least Expect It
What surprises customers most is just how much real, exploitable risk hides in their own code, even when their open-source dependencies and repositories look clean.
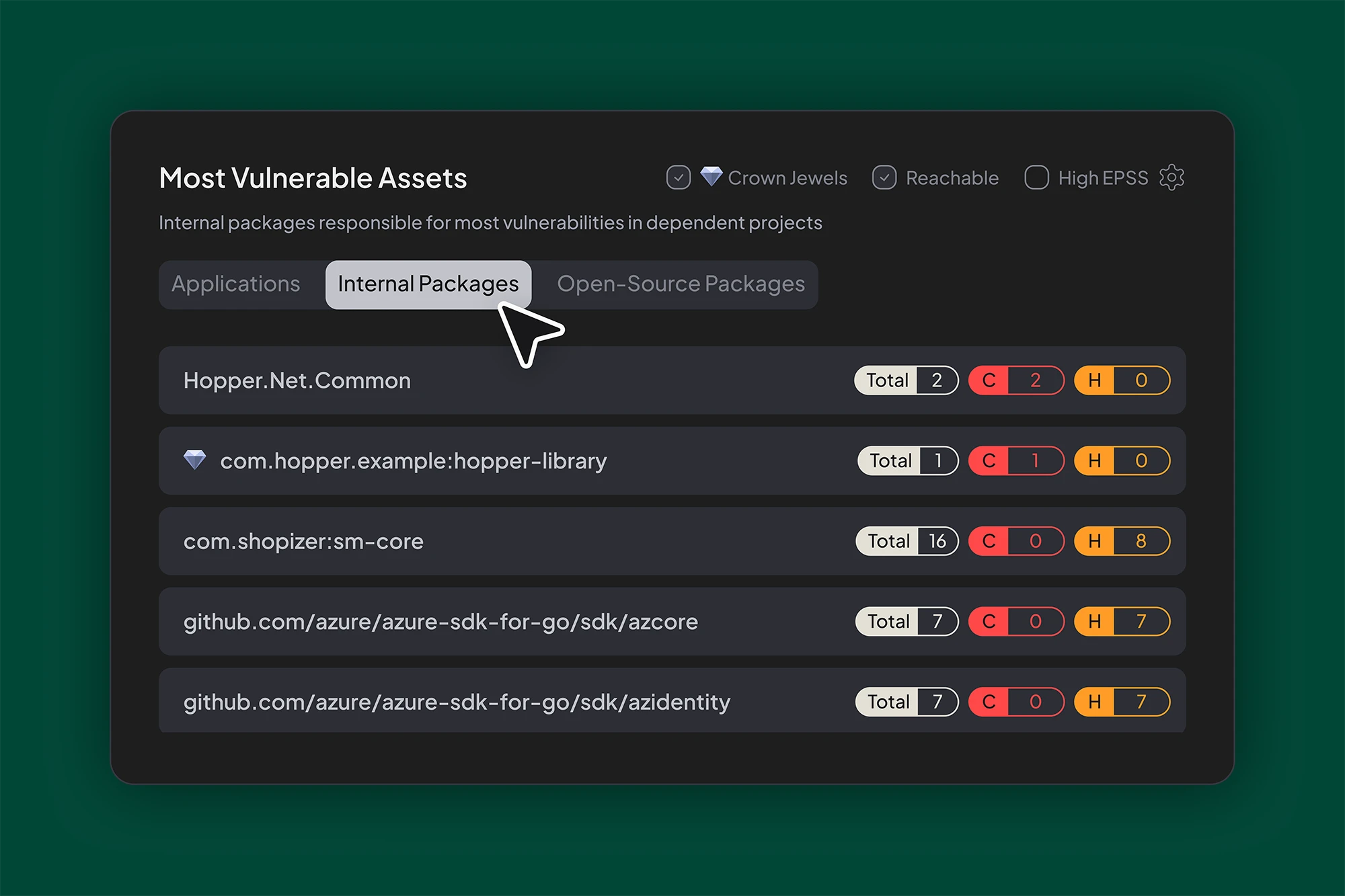
Internal libraries are everywhere. Stored in systems like JFrog Artifactory, Sonatype Nexus, or Azure Artifacts, they power core functionality across services. Think of packages like com.acme.messaging, com.acme.logging, com.acme.auth, or com.acme.crypto.
They are usually maintained by platform teams who do a great job keeping the latest versions patched and up to date. But most tools only scan the latest version. They don't show which applications are still relying on older, vulnerable versions that continue to exist in the artifact store.
The result is a hidden exposure. The repository looks clean. The latest artifact version is safe. But the outdated version is still being used in production.
When Container Scanning or Runtime Tools Find It First
This visibility gap leads to confusion and wasted time.
Runtime tools might flag a vulnerability. But when engineers try to track it down, the repository shows a patched version. The SCA scan is clean. The artifact registry appears fine. And yet, something in production is still triggering the alert.
Without visibility into actual usage, teams can't trace the issue to its source. These cases often get dismissed as false positives, even though the risk is real and active.
How Hopper Closes the Loop
We just released a short demo showing exactly how Hopper solves this problem.
Hopper maps which internal libraries are being used, identifies which versions are in play, and traces vulnerable call paths back to the source. It correlates reachability and EPSS data to prioritize the risks that matter most. And it gives teams a clear, actionable view of what is vulnerable, where, and why.
In one case, a Fortune 500 customer discovered that a Java library they believed was patched was still being pulled into dozens of builds through an outdated artifact. Hopper identified the issue, traced the vulnerable code path, and showed exactly which services were affected.
Internal Risk, Quantified
This is not rare. In a real-world analysis of that same Fortune 500 customer:
64.16% of all function-level reachable critical and high-severity vulnerabilities originated from internally developed libraries.
Not open-source. Not third-party. Their own infrastructure code.
That distinction matters. Internal code doesn’t just carry risk. It amplifies it, because it's everywhere. Without a way to track and prioritize these libraries, teams are left chasing ghosts, or worse, ignoring real threats.
The Blind Spot You Can’t Ignore
In many environments, more than 50% of open-source risk comes from internal libraries. This is more than a visibility problem. It is a critical attack surface that Hopper helps you monitor, analyze, and secure.
The Hopper demo shows exactly how we help teams uncover what is missed and take action before risks escalate. What was once invisible becomes clear, traceable, and prioritized.
Want to know what your internal libraries are really exposing you to? Schedule a walkthrough of how Hopper can help you identify internal risks.