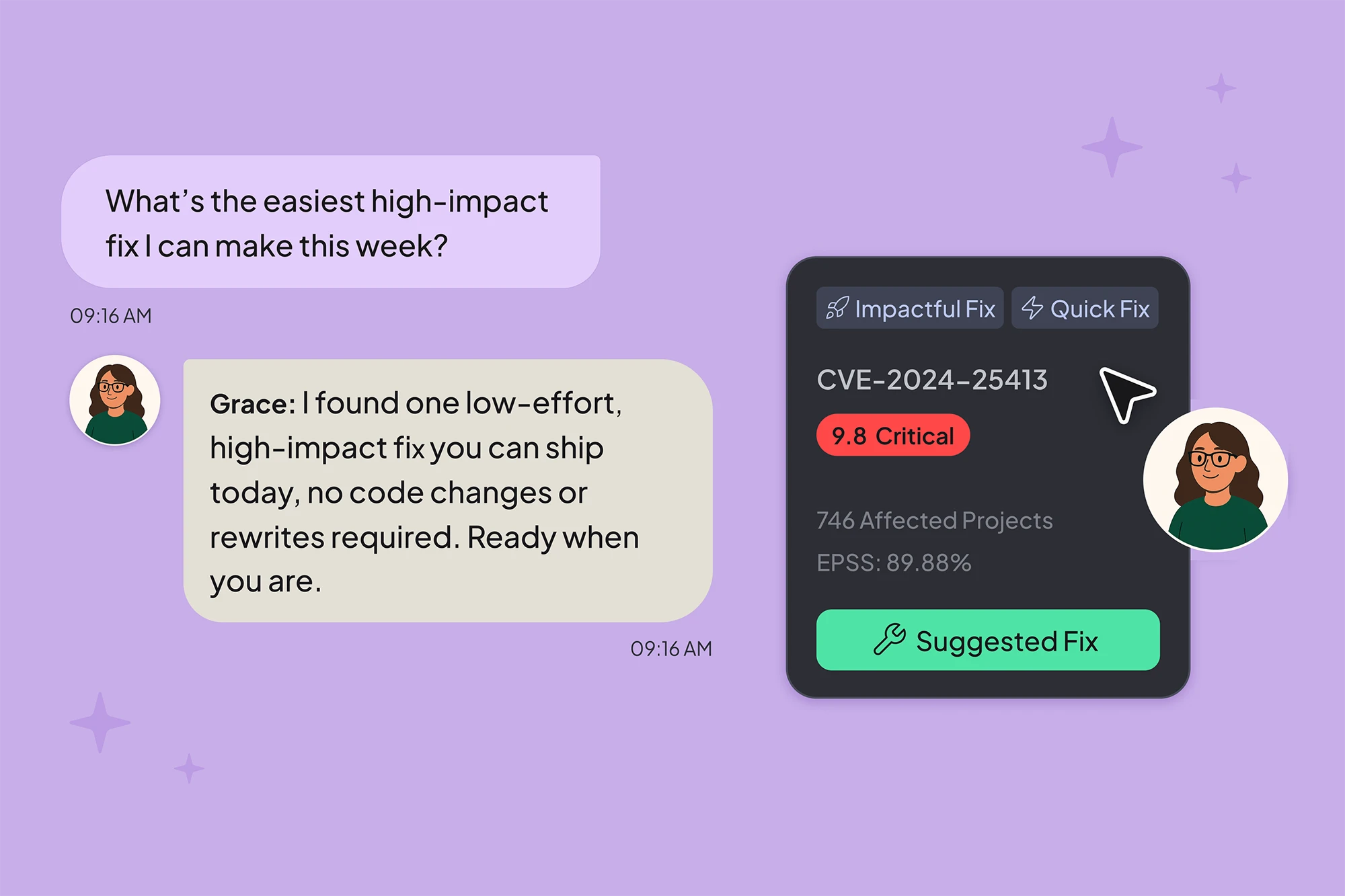
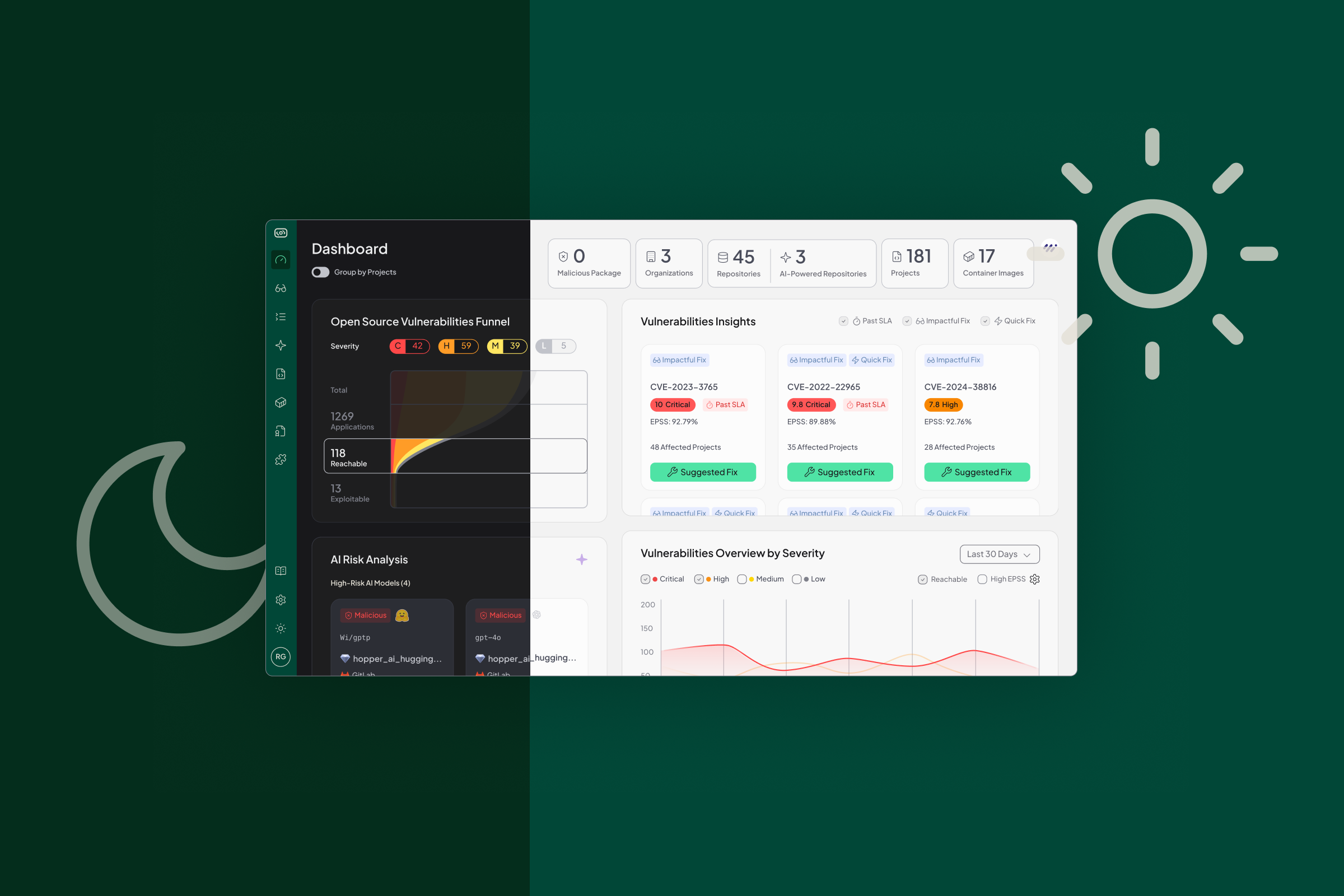
Meet Grace, Hopper’s new MCP server that turns your open-source security data into intelligent action. Grace connects Hopper’s trusted insights, your source code, and the power of AI agents, automating everything from vulnerability triage to hands-free remediation using natural language.
What Is MCP?
On November 25, 2024, Anthropic introduced the Model Context Protocol (MCP), a universal standard for connecting AI assistants with tools, services, and data.
That announcement reshaped the world of LLMs and agent-based workflows. Instead of treating LLMs as isolated oracles, MCP enables them to function as dynamic agents with access to real-time systems and knowledge.
How MCP Works
MCP follows a client-server model:
- An MCP client (like Claude, Cursor, or Cline) runs on your machine.
- It connects to one or more MCP servers, each exposing tools, services, or datasets through a standardized protocol.
- When you submit a prompt, the client sends it to the connected servers, identifies which integration can handle it, and executes the task.
- For complex workflows, MCP chains requests across services to enable multi-step automation.
Visualized:

Meet Grace: Hopper’s MCP Server
Grace is Hopper’s native MCP server. It gives AI agents secure access to live vulnerability data, including reachability evidence and call graph, AI model usage, licenses, container risks, and more.
Your AI copilots can now go beyond answering questions. They can reason over Hopper insights, take action, and automate remediation.
From Insight to Action
Hopper is built to provide real-time open-source security data. But data alone isn’t enough. The next frontier is automation.
Grace makes your Hopper data operational. AI agents can:
- Analyze vulnerability impact using function-level reachability.
- Query application metadata and license usage.
- Launch actions such as fix generation or PR creation.
Your security knowledge base becomes an automation engine.
Ask Grace Anything

Grace understands natural language. Try questions like:
- Which of my most critical apps are currently the most vulnerable?
- Am I impacted by CVE-2021-44228 (Log4J)?
- Which vulnerabilities have missed their remediation SLA?
- Are any applications using AGPL-licensed dependencies?
- List all applications using AI.
Grace will respond with:
- Reachability call graphs
- Fix plans and effort estimates
- Evidence and explanations
- License breakdowns
Grace Takes Action
Grace doesn’t just detect risk. She fixes it. Try:
- Fix the critical vulnerabilities in repo
<YourRepoName> - Remediate CVE-2021-44228
Grace will:
- Generate code and manifest updates based on Hopper’s fix plan
- Help you open a pull request
- Remove the vulnerability with minimal manual effort
Get Started in Minutes
Developers can connect Grace to their favorite IDEs that support local MCP (like Cursor or Cline) in under 5 minutes.
- Get your Grace MCP configuration block.
- Open your MCP client, go to Settings → MCP Servers.
- Paste the config block and click Save.
That’s it. Your client will now:
- Automatically discover tools exposed by Grace
- Select the right resource for your request
- Handle security tasks behind the scenes
No complex docs. No manual routing. Just plug and go.
Connect More MCP Servers
Grace works alongside other MCP servers. Want to push tickets to Jira or trigger notifications in Slack? Just connect those servers too.
Example:
Find all reachable vulnerabilities and create Jira tickets for each, including fix plans and evidence.
The client will:
- Use Hopper MCP to gather vulnerabilities
- Use Jira MCP to open the tickets
- Execute the workflow automatically
You now have an assistant that knows your environment, takes action, and accelerates resolution across systems.
Ready to Ask Grace?
From reachability analysis to fix deployment, Grace helps you move faster, work smarter, and stay ahead of open-source risks. Try it now or schedule a demo.
Appendix: What’s Happening Behind the Scenes?
Grace exposes Hopper’s security capabilities through standard MCP interfaces. These include:
- Structured queries for vulnerabilities and licenses
- Function-level reachability data
- Fix plan generation APIs
- SBOM and legal tooling endpoints
Each integration is documented and schema-based, so your MCP client knows which tools to call and what to expect in return. You don’t need to think in API calls. You just describe what you want.