Trace And Fix Every
Exploitable Vulnerability in
Exploitable Vulnerability in
|
Use AI agents and function-level traces to confirm exploitability, prioritize action, and accelerate response across every application you build, buy, or use.
Start Free Today
30 days free. No credit card required. Includes 5 container scans.
How Hopper Transforms Vulnerability Response
Prove What’s Exploitable
Combine function-level traces with AI reasoning to investigate and validate impact.
Accelerate Response
Identify affected assets instantly, publish advisories faster, remediate with ease, and meet customer commitments.
Respond Across Every Artifact
Analyze and protect binaries, containers, and repositories, across every application your business builds, buys, or uses.

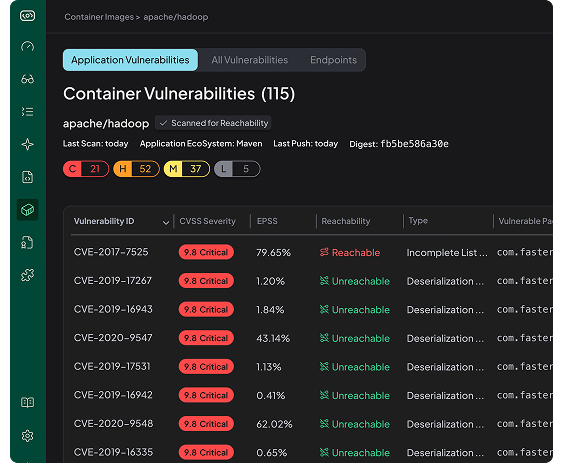
Container Image Analysis
Application-Layer Vulnerabilities detected in commonly used public container images.
View All Containers
apacheignite/ignite:latest
Digest:
sha256:9b350ea397b5e64d5ff2baddf0205049527a135e4526ab4e0b88fdf6fc7876bd
Application Vulnerabilities
C
1
H
10
M
9
L
1
Reachable Vulnerabilities Only
C
0
H
5
M
3
L
0
↓
61.9
Noise Reduced
confluentinc/cp-server:7.0.0
Digest:
sha256:d0ba7b41e5a64dae454b6f6ee25de0d5641e716631ba4765dba4ddfe90aa0f2d
Application Vulnerabilities
C
5
H
51
M
78
L
11
Reachable Vulnerabilities Only
C
3
H
30
M
26
L
2
↓
57.9
Noise Reduced
graviteeio/apim-gateway:4.3
Digest:
sha256:43cb4e3d9638caf6f138368906b74af6a96c811c7bb213d7af5c3d907076dc9a
Application Vulnerabilities
C
0
H
3
M
16
L
4
Reachable Vulnerabilities Only
C
0
H
2
M
5
L
3
↓
56.5
Noise Reduced