Container Vulnerabilities
Use AI agents and function-level traces to confirm exploitability, prioritize action, and accelerate response across every application you build, buy, or use.
Start Free Today
30 days free. No credit card required.
Includes 5 container scans.

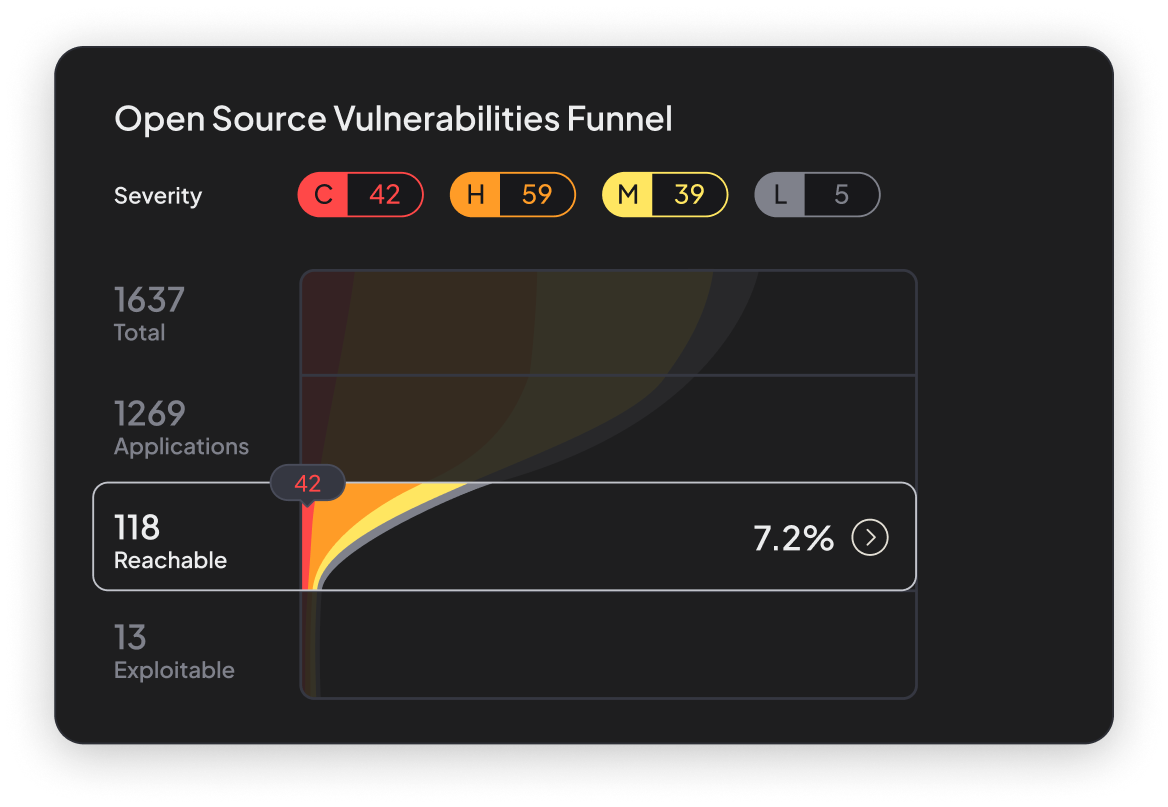
See the Difference Verified Exploitability Makes
Capability
Hopper
Traditional SCA
Reachability Analysis
Function-level call path detection
Flags entire packages
Exploitability Context
EPSS, KEV, the presence of available exploit and other signals layered on top
Varies by tool; some offer basic CVSS severity only
Noise Reduction
93% fewer irrelevant alerts
High volume of unprioritized findings
Deployment Model
Agentless, read-only Git integration
Varies by tool; some offer agentless modes but often require build integration or CLI use
Hidden Dependence Detection
Identifies renamed, repackaged, and shaded libraries
Often missed or misclassified