Trace And Fix Every
Exploitable Vulnerability in
Exploitable Vulnerability in
|
Use AI agents and function-level traces to confirm exploitability, prioritize action, and accelerate response across every application you build, buy, or use.
Start Free Today
30 days free. No credit card required. Includes 5 container scans.
How Hopper Transforms Vulnerability Response
Prove What’s Exploitable
Combine function-level traces with AI reasoning to investigate and validate impact.
Accelerate Response
Identify affected assets instantly, publish advisories faster, remediate with ease, and meet customer commitments.
Respond Across Every Artifact
Analyze and protect binaries, containers, and repositories, across every application your business builds, buys, or uses.

Container Image Analysis
Application-Layer Vulnerabilities detected in commonly used public container images.
View All Containers
apache/spark:3.5.7
Digest:
sha256:3d864798d744013fe002188f513307dc4ba43896b7983e21ccd4e9ba6f7cf6b9
Application Vulnerabilities
C
2
H
26
M
33
L
7
Reachable Vulnerabilities Only
C
0
H
7
M
1
L
3
↓
83.8
Noise Reduced
library/neo4j:5.21.0-enterprise-ubi9
Digest:
sha256:e1de83e5592894a18a1102d53886f4d8853c015393650121a76728cc5e0f82b9
Application Vulnerabilities
C
0
H
7
M
12
L
2
Reachable Vulnerabilities Only
C
0
H
1
M
3
L
0
↓
81
Noise Reduced
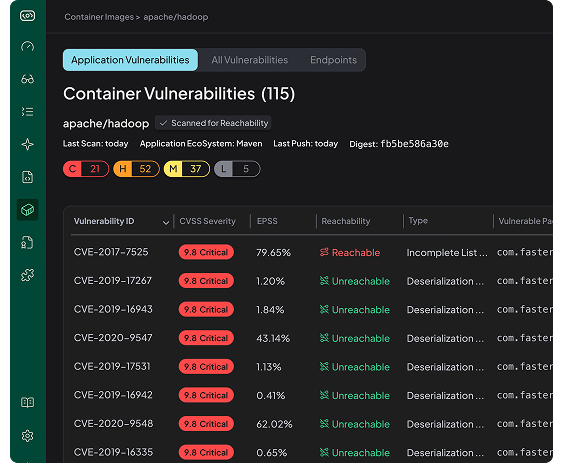
apache/hadoop:3.4
Digest:
sha256:69ffa97339aff768c4e6120c3fb27aa04c121402b1c8158408a5fb5be586a30e
Application Vulnerabilities
C
21
H
52
M
37
L
5
Reachable Vulnerabilities Only
C
4
H
12
M
4
L
2
↓
80.9
Noise Reduced