Trace And Fix Every
Exploitable Vulnerability in
Exploitable Vulnerability in
|
Use AI agents and function-level traces to confirm exploitability, prioritize action, and accelerate response across every application you build, buy, or use.
Start Free Today
30 days free. No credit card required. Includes 5 container scans.
How Hopper Transforms Vulnerability Response
Prove What’s Exploitable
Combine function-level traces with AI reasoning to investigate and validate impact.
Accelerate Response
Identify affected assets instantly, publish advisories faster, remediate with ease, and meet customer commitments.
Respond Across Every Artifact
Analyze and protect binaries, containers, and repositories, across every application your business builds, buys, or uses.

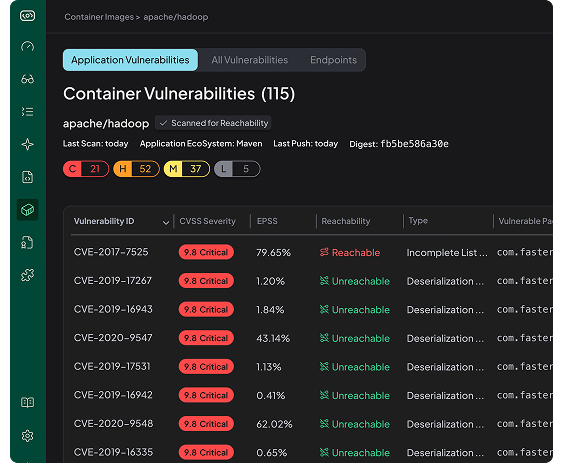
Container Image Analysis
Application-Layer Vulnerabilities detected in commonly used public container images.
View All Containers
atlassian/bitbucket:latest
Digest:
sha256:9eda051ba7244f77e5c286f6a7b00f8a4baec7dbfd09dd030b6d900dc04f62dc
Application Vulnerabilities
C
0
H
3
M
5
L
0
Reachable Vulnerabilities Only
C
0
H
1
M
3
L
0
↓
50
Noise Reduced
library/cassandra:5.0.5
Digest:
sha256:e473005c1eb66295e93a38cfada93ae6492189ace27db8712592941bf7190e9a
Application Vulnerabilities
C
0
H
9
M
9
L
1
Reachable Vulnerabilities Only
C
0
H
5
M
6
L
0
↓
42.1
Noise Reduced
apereo/cas:7.2.7
Digest:
sha256:05977120bbdc236e1bdad1fcbf0108c16d9b5a68e28427ce4aa5fc7d3059c702
Application Vulnerabilities
C
2
H
12
M
9
L
2
Reachable Vulnerabilities Only
C
2
H
8
M
7
L
2
↓
24
Noise Reduced