Changes on the Horizon
On August 21, 2025, Federal Risk and Authorization Management Program (FedRAMP) closed public comment on RFC-0012, its proposed Continuous Vulnerability Management Standard. While still in draft, the standard represents a significant shift in how the standard represents a major shift in how security is measured across the federal ecosystem.
The focus is no longer on box-checking and CVSS scores. Success will be judged by whether vulnerabilities are exploitable in context, prioritized appropriately, and remediated within days instead of weeks or months. The impact extends well beyond traditional cloud service providers (CSPs): SaaS vendors, cloud platforms, defense contractors, and technology suppliers throughout the federal supply chain will all be expected to align with these requirements.
Executive Takeaway: FedRAMP is redefining vulnerability management from a compliance exercise into a real-time measure of security effectiveness. Organizations that cannot prove continuous, contextualized remediation will struggle to maintain authorizations and ultimately market access.
What’s New in RFC-0012
At its core, the RFC introduces four transformative ideas:
1. From Scores to Context
Vulnerability management is no longer just about a CVSS number. Providers must factor in reachability, exploitability, impact, prevalence, and mitigation to determine if a weakness is “credibly exploitable.” This aligns more closely with how attackers actually operate and how engineering teams already prioritize work.
2. Aggressive Timelines
The new standard accelerates remediation windows dramatically.
- 3 days to mitigate or remediate internet-reachable, credibly exploitable vulnerabilities
- 7 to 21 days for internal systems, depending on severity
- 6 months for all remaining vulnerabilities
- See the proposed timelines in the Appendix below
By comparison, FedRAMP’s prior guidance allowed up to 30 days for criticals and 90 days for highs, meaning the RFC cuts expected response times by up to 10X. For many CSPs, this will require automation and continuous triage to even approach compliance.
3. Automation and Reporting
Monthly (ideally continuous) machine- and human-readable vulnerability reports must be provided to FedRAMP, CISA, and government agencies. While SBOMs may play a role, the expectation is likely broader: API-driven feeds that give agencies near real-time visibility into remediation progress.
4. POA&M Reform
Plans of Action & Milestones (POA&Ms) have long been one of the most time-consuming aspects of FedRAMP compliance, with providers required to track nearly every open vulnerability in a spreadsheet-like artifact. POA&Ms will now be used only when issues cannot be remediated within prescribed timelines.
This is more than a paperwork change. It shifts accountability from documenting vulnerabilities to actually fixing them, with POA&Ms reserved for true exceptions. For executives, that means reduced administrative overhead but also fewer opportunities to defer action. The expectation is clear: vulnerabilities must be resolved, not just recorded.
What the Industry Said
Public comments show strong support for FedRAMP’s new direction, but also highlight pressure points that will likely shape the final rule. Many welcomed the shift away from CVSS-only scoring toward a model that prioritizes exploitability, reachability, and business impact. Automation was seen as essential to meet the new timelines, and limiting POA&Ms to true exceptions was praised as a way to reduce administrative overhead.
Respondents also flagged practical challenges:
- Timelines: The 3-day SLA for internet-facing vulnerabilities was widely viewed as unrealistic in complex environments, especially when patches depend on vendors or resources are constrained.
- Defining exposure: In microservices and cloud-native architectures, mapping what is truly internet-facing is difficult, since exposure is often fluid and obscured.
- Ambiguity: Terms like “credibly exploitable” and “internet-reachable” remain unclear, creating room for friction between providers, assessors, and agencies.
- Automation risks: Without guardrails, automation could cause outages.
- Disclosure risks: Requiring disclosure of unmitigated vulnerabilities could inadvertently expose federal systems to attackers.
- Infrastructure mitigations: Some argued that isolation or segmentation should count toward reducing exploitability, even before patches are applied.
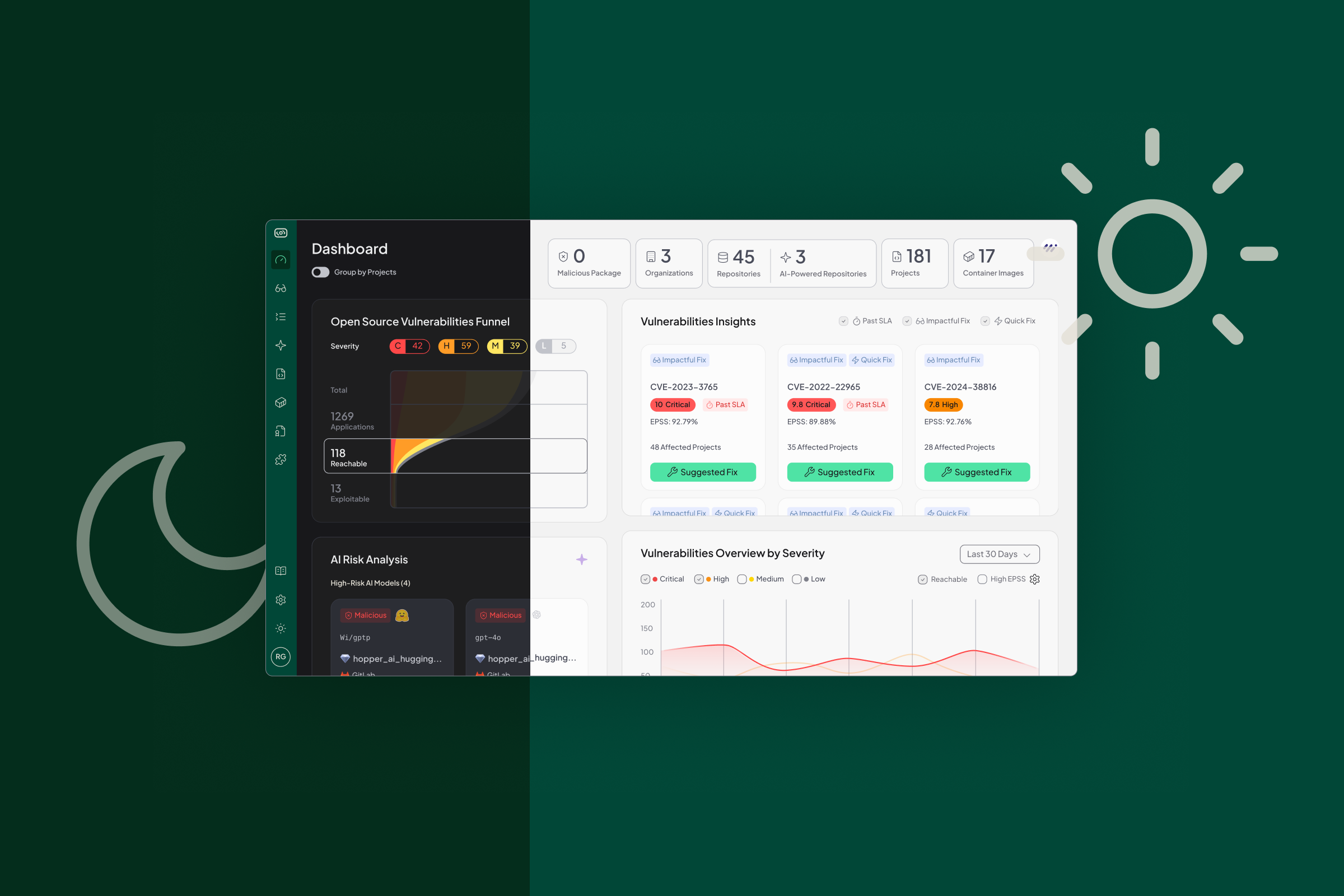
Hopper’s view: the core direction of RFC-0012 is correct. Vulnerability management must evolve from theoretical CVSS scores to context and exploitability, and automation is the only path to meeting real-world timelines. Where the standard will likely bend is on the strictness of timelines and the clarity of definitions, but not on the underlying expectation that providers prove exploitability and continuously report on outcomes. This is exactly the kind of evidence-based prioritization that Hopper delivers through function-level reachability, which shows whether a vulnerability is truly exploitable in a given application.
Why This Matters for Executives
The FedRAMP RFC is not just a compliance change. It represents a new baseline for how governments and enterprises expect risk to be managed.
- Compliance Converges with Security — This is less about producing reports and more about demonstrating real risk reduction in real time.
- Operational Impact — Teams will need to adopt automated asset discovery, contextual risk scoring, and continuous reporting. Manual approaches cannot keep pace with 3, 7, or 21-day windows.
- Cultural Change — Security programs must prove not just that vulnerabilities exist, but whether they are exploitable in context. Evidence-based findings are critical to getting developer buy-in and reducing wasted cycles.
- Customer Pressure — Federal agencies, and increasingly large enterprises, will demand transparency. Expect to see continuous dashboards and data feeds, not static reports.
This is exactly the type of environment where Hopper delivers value. Our function-level reachability and contextual analysis reduce vulnerability noise by more than 93%, ensuring security teams and developers focus only on what matters most.
Executive Takeaways
- Plan for Automation: Continuous scanning, contextual risk analysis, and machine-readable reporting are becoming the norm.
- Rethink POA&Ms: Exceptions will be scrutinized. “Just file a POA&M” is no longer viable.
- Balance Speed and Stability: Meeting timelines requires automation, but not at the expense of availability. Leadership must set expectations for both.
- Invest in Contextual Security: Reachability and exploitability matter more than raw counts. This is the new language of both regulators and attackers.
- Anticipate Spillover: What starts in FedRAMP often becomes a broader market expectation. Continuous vulnerability management is poised to become table stakes for enterprise companies.
The Road Ahead
FedRAMP will revise RFC-0012 and pilot it under the 20x initiative and Rev5 Beta tests before full rollout. Executives should begin assessing:
- How quickly their organization could comply with a 3-day remediation SLA
- Whether current reporting can shift to continuous, machine-readable formats
- How to embed reachability and exploitability context into risk prioritization
Final Thoughts
RFC-0012 signals the end of the divide between “security for compliance” and “security for reality.” FedRAMP is making it clear: only vulnerabilities that matter should demand engineering time, and those must be addressed faster than ever before.
At Hopper, we help security leaders get there. Our function-level reachability, automation, and compliance-ready reporting give executives confidence that teams are focusing on real risks and meeting the standards of tomorrow, today.