Trace And Fix Every
Exploitable Vulnerability in
Exploitable Vulnerability in
|
Use AI agents and function-level traces to confirm exploitability, prioritize action, and accelerate response across every application you build, buy, or use.
Start Free Today
30 days free. No credit card required. Includes 5 container scans.
How Hopper Transforms Vulnerability Response
Prove What’s Exploitable
Combine function-level traces with AI reasoning to investigate and validate impact.
Accelerate Response
Identify affected assets instantly, publish advisories faster, remediate with ease, and meet customer commitments.
Respond Across Every Artifact
Analyze and protect binaries, containers, and repositories, across every application your business builds, buys, or uses.

Container Image Analysis
Application-Layer Vulnerabilities detected in commonly used public container images.
View All Containers
apachepinot/pinot:1.4.0-17-amazoncorretto
Digest:
sha256:83186d8c9ab4a289c8e3dafec04c18fcb776304256e630b859cc41b4ca7219a1
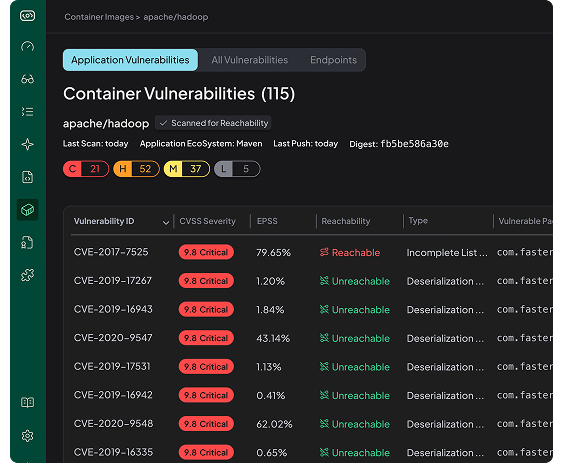
Application Vulnerabilities
C
0
H
2
M
5
L
1
Reachable Vulnerabilities Only
C
0
H
0
M
0
L
0
↓
100
Noise Reduced
jenkins/jenkins:2.520-alpine
Digest:
sha256:4b04591503d37df95539b2411873fd39d96562b0df7a4ce8bcdd825935db7f98
Application Vulnerabilities
C
0
H
6
M
12
L
0
Reachable Vulnerabilities Only
C
0
H
0
M
0
L
0
↓
100
Noise Reduced
keycloak/keycloak:26.2.5
Digest:
sha256:e1bea10dc9a144b0f70aba477ba2ef14a0fa752e7e95faa4b7903ffa1287187a
Application Vulnerabilities
C
0
H
4
M
14
L
3
Reachable Vulnerabilities Only
C
0
H
0
M
0
L
0
↓
100
Noise Reduced